# Build a Top 10 mod
> Here's how to build a mod to check the top 10 AWS security tips. You can use this pattern to build your own custom mods to check other Top 10 lists.
By Steampipe Team
Published: 2023-07-18
In [Top 10 security items to improve in your AWS account](https://aws.amazon.com/blogs/security/top-10-security-items-to-improve-in-your-aws-account/), on the [AWS Security Blog](https://aws.amazon.com/blogs/security/), Nathan Case writes:
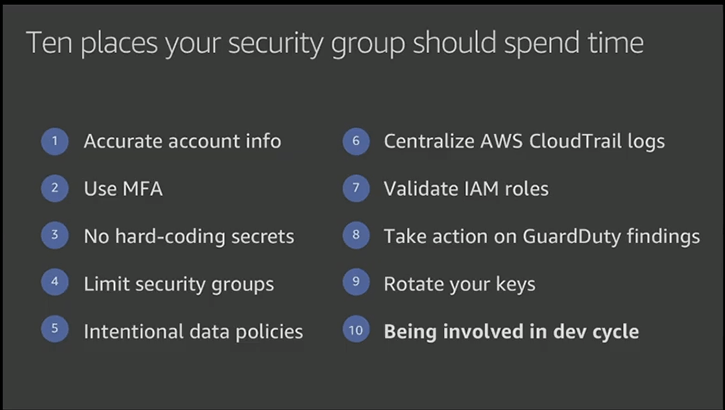
> If you're looking to improve your cloud security, a good place to start is to follow the top 10 most important cloud security tips that Stephen Schmidt, Chief Information Security Officer for AWS, laid out at AWS re:Invent 2019. Below are the tips, expanded to help you take action.
We agree! Let's look at how Steampipe can help you follow that advice. We'll develop a Steampipe benchmark that runs relevant controls — from mods like [AWS Compliance](https://hub.steampipe.io/mods/turbot/aws_compliance) and [AWS Perimeter](https://hub.steampipe.io/mods/turbot/aws_perimeter) — and produces a detailed report for all your accounts and regions.
## Find relevant controls
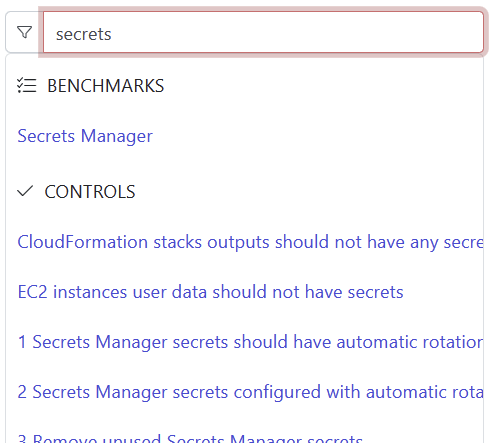
The AWS Compliance mod is a rich source of controls that implement checks required by a broad set of frameworks and standards. On the Steampipe Hub's [controls page](https://hub.steampipe.io/mods/turbot/aws_compliance/controls) you can search for words that relate to a given security tip, for example `secrets` finds controls relevant to tip 3, *No hard-coding secrets*.
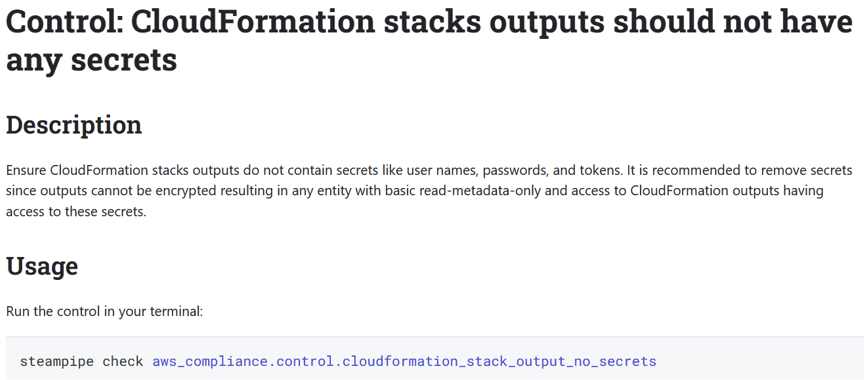
In this case, the first result is [CloudFormation stacks outputs should not have any secrets](https://hub.steampipe.io/mods/turbot/aws_compliance/controls/control.cloudformation_stack_output_no_secrets).
It's clearly relevant, so we'll put its name — `aws_compliance.control.cloudformation_stack_output_no_secrets` — on our list.
Following the same approach, you can build up sets of control names relevant to each of the tips. Then it's time to roll them into a custom benchmark.
## Create the benchmark skeleton
First, make and visit a directory.
```
$ mkdir aws-security-top-10
$ cd aws-security-top-10
```
Then, because this mod will use controls defined in the AWS Compliance mod, run the [steampipe mod install](https://steampipe.io/docs/reference/cli/mod) command to create a hidden local copy of that mod.
```
$ steampipe mod install github.com/turbot/steampipe-mod-aws-compliance
Installed 1 mod:
local
└── github.com/turbot/steampipe-mod-aws-compliance@v0.72.0
```
The command also creates an initial `mod.sp` file.
```
mod "local" {
title = "aws-security-top-10"
require {
mod "github.com/turbot/steampipe-mod-aws-compliance" {
version = "*"
}
}
}
```
You can change the title there to, for example, "AWS Top 10".
Now create another file, `top-10.sp`, in which to define the benchmark. Here's an initial skeleton.
```
benchmark "aws_top_10" {
title = "AWS Top 10"
description = "Controls relevant to the top 10 security items."
children = [
benchmark.accurate_account_info,
benchmark.use_mfa,
benchmark.no_secrets,
benchmark.limit_security_groups,
benchmark.intentional_data_policies,
benchmark.centralize_cloudtrail_logs,
benchmark.validate_iam_roles,
benchmark.take_action_on_findings,
benchmark.rotate_keys
]
}
benchmark "accurate_account_info" {
title = "1. Accurate account information"
children = [
]
}
benchmark "use_mfa" {
...
}
```
A benchmark can contain benchmarks which in turn contain controls. The skeleton defines a top-level benchmark that enumerates a child benchmark for each of the security items. Each child benchmark has a list — initially empty -- of the controls we've gathered.
## Put meat on the bones
Now it's just a matter of populating the lists with the names of the controls we've gathered. For example:
```
benchmark "use_mfa" {
title = "2. Use multi-factor authentication (MFA)"
children = [
aws_compliance.control.iam_root_user_mfa_enabled,
aws_compliance.control.iam_user_mfa_enabled,
aws_compliance.control.iam_user_console_access_mfa_enabled,
]
}
```
Note that the AWS Compliance mod isn't the only source for controls. As we went through the list, we realized that [AWS Perimeter](https://hub.steampipe.io/mods/turbot/aws_perimeter) would have relevant controls too, such as [IAM role trust policy policies should prohibit public access](https://hub.steampipe.io/mods/turbot/aws_perimeter/controls/control.iam_role_trust_policy_prohibit_public_access). To use some of them, run [steampipe mod install](https://steampipe.io/docs/reference/cli/mod) again to gain access to them.
```
$ steampipe mod install github.com/turbot/steampipe-mod-aws-perimeter
Installed 1 mod:
local
└── github.com/turbot/steampipe-mod-aws-perimeter@v0.3.0
$ steampipe mod list
local
├── github.com/turbot/steampipe-mod-aws-compliance@v0.72.0
└── github.com/turbot/steampipe-mod-aws-perimeter@v0.3.0
```
Now we can refer to controls in both installed mods.
```
benchmark "validate_iam_roles" {
title = "7. Validate IAM roles"
children = [
aws_compliance.control.cis_v150_1_20,
aws_compliance.control.iam_access_analyzer_enabled_without_findings,
aws_perimeter.control.iam_role_trust_policy_prohibit_public_access
]
}
```
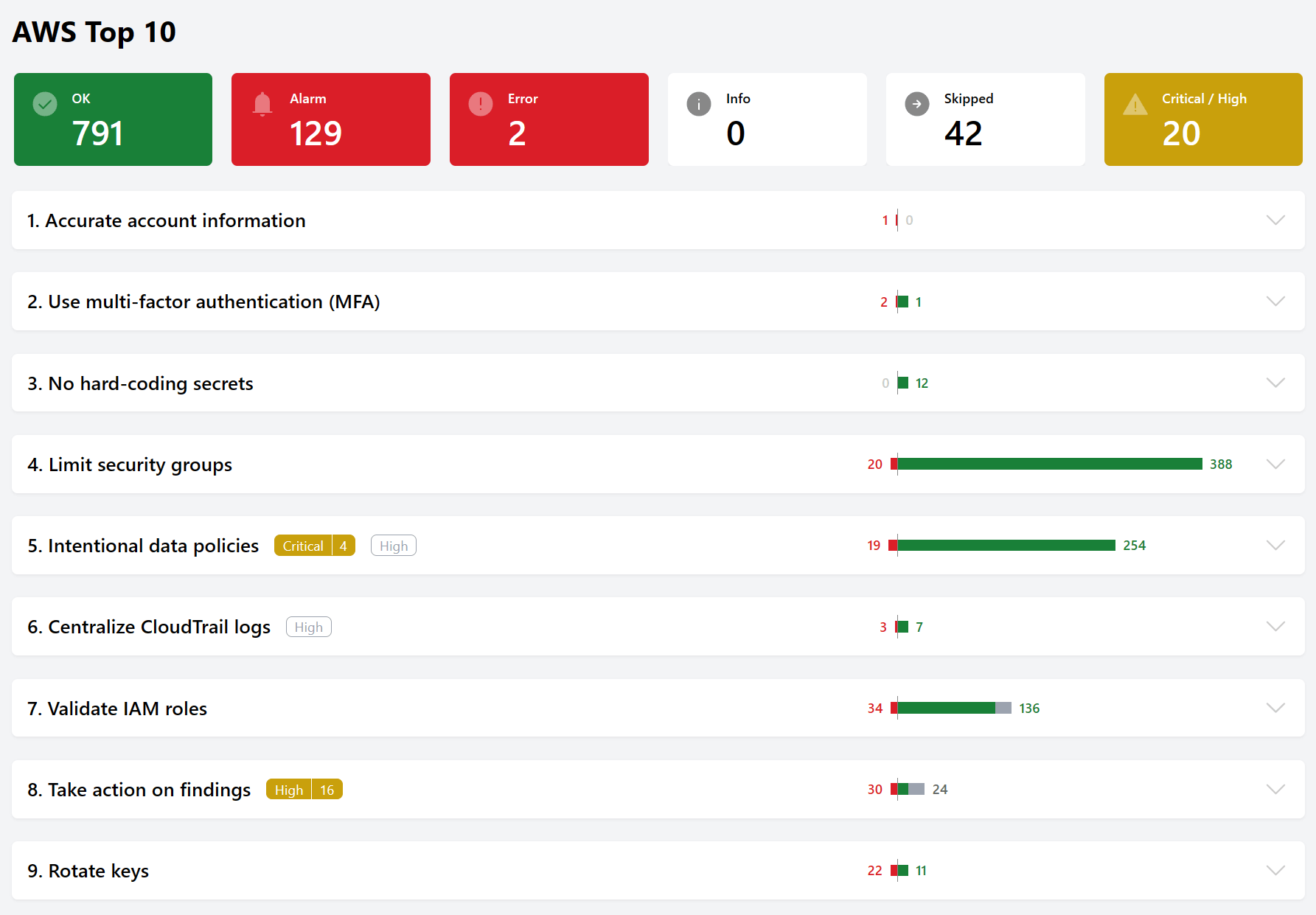
## Run the benchmarks
To run the benchmark in your terminal:
```
$ steampipe check all
```
To run the benchmark in your browser, run `steampipe dashboard` and visit `https://localhost:9194`.
## Share the benchmark report
To share the report on Steampipe Cloud, first [login](https://steampipe.io/docs/reference/cli/login). Then:
```
steampipe dashboard --share benchmark.aws_top_10
Snapshot uploaded to https://cloud.steampipe.io/user/
udell/workspace/personal/snapshot/snap_cib1atb9rqbm1gfe1n10_04d5drrmy96xt3q63qhyhwweau
```
You can now view the benchmark at that URL, and you can [share](https://steampipe.io/docs/cloud/dashboards#saving--sharing-snapshots) the view with anyone you've invited into the workspace, or anyone to whom you give the URL.
## Where's #10?
We didn't include controls for `Tip #10: Being involved in the dev cycle` because none (as yet) are relevant. Instead, we'll humbly suggest a best practice: Use Steampipe! It's a great way to monitor your security posture and assure that it remains continuously effective.
## Next steps
We initially built this mod as tutorial, then the team decided to adopt it as an [offical mod](https://github.com/turbot/steampipe-mod-aws-security-top-10). We can imagine other Top 10 benchmarks, but we're sure you can too. If you build one, and would like to include it in the Steampipe hub, please [let us know](https://steampipe.io/community/join)!