{`
select
arn as "Buckets without MFA Delete"
from
aws_s3_bucket
where
not versioning_mfa_delete
and tags->>'data-class' in ('med', 'high');
`}
{`
+---------------------------------------+
| Buckets without MFA Delete |
+---------------------------------------+
| arn:aws:s3:::dmi-employee-data |
| arn:aws:s3:::dmi-data-lake-metadata |
| arn:aws:s3:::paper-competitive-intel |
| arn:aws:s3:::test-principal-wildcard |
+---------------------------------------+
`}
- **2.3.1 Enforce RDS encryption** — Most surprising thing about this to me is that this is the first RDS check for CIS... A lot more opportunity space here.
- **3.5 Implementing AWS config in all regions** — Was moved to a level 2 control because there is additional cost associated with enabling it.
- **1.12 Unused credentials time limit changed from 90 days to 45** — This stemmed from new guidance in CIS Controls v8. It always struck me that 90 days is arbitrarily long for this, 6 weeks seems like a reasonable time period that balances productivity vs security a bit better.
- **2.1.5 Ensure Amazon S3 has been discovered, classified and secured 'when required'** — This is a new recommendation to ensure all data is classified via automated analysis. The remediation section just shows how to enable Amazon Macie for your buckets, but many orgs will have their own tooling/approach here.
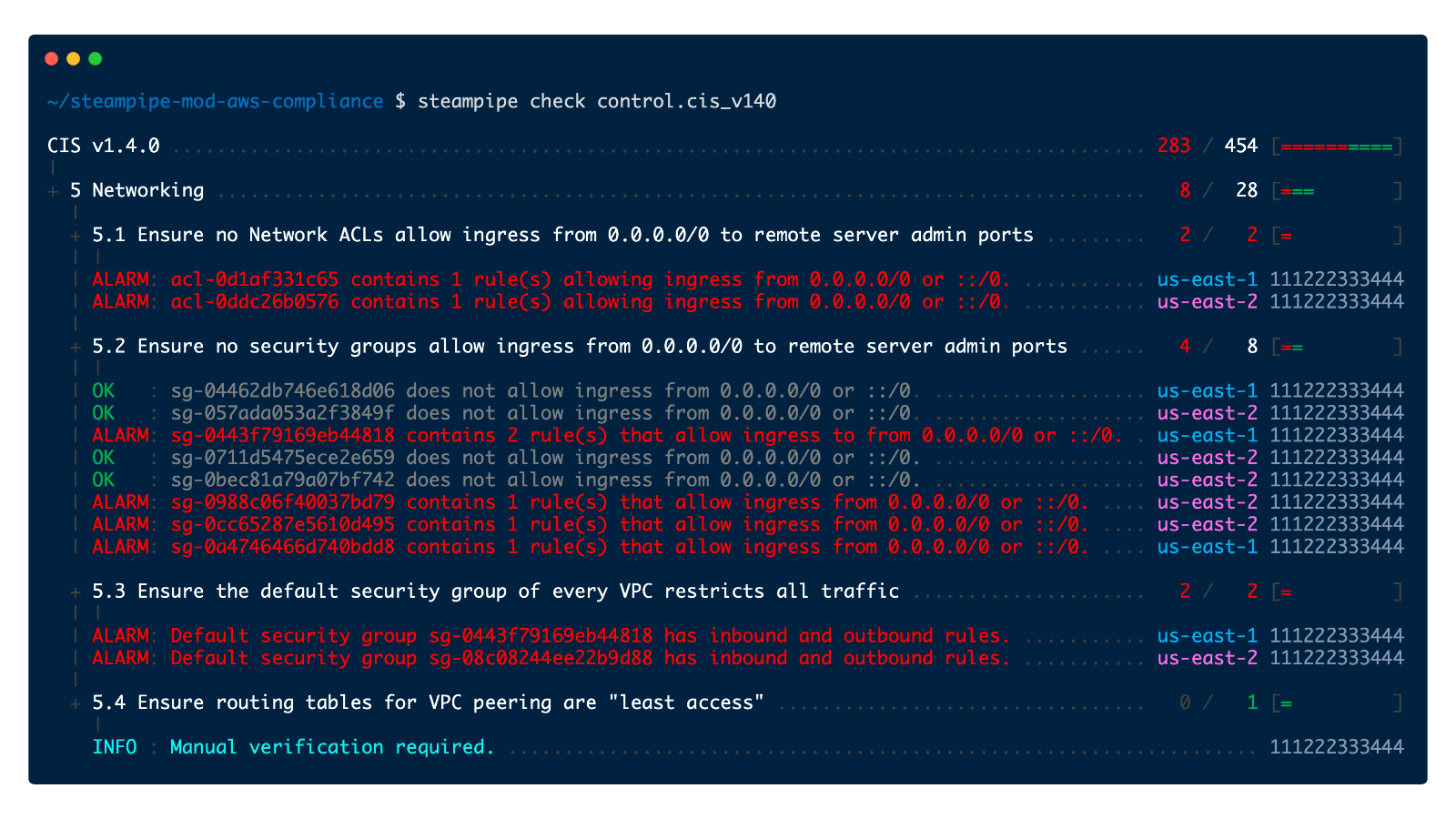
The rest of the changes were mainly typos and changes to audit/remediation procedures. The open source [Steampipe AWS compliance mod has codified the changes in this repo](https://github.com/turbot/steampipe-mod-aws-compliance). If you want to run a quick v1.4 scan on your account, clone the repo locally and run from the CLI:
 ## We love open source!
Steampipe now delivers a full suite of tools to build, execute and share cloud configuration, compliance, and security frameworks using SQL, HCL and a little elbow grease! We would love your help to expand the open source documentation and control coverage for CIS, PCI, HIPAA, NIST… and the best way to get started is to [join our new Slack workspace](https://steampipe.io/community/join) and raise your hand; we would love to talk to you!
## We love open source!
Steampipe now delivers a full suite of tools to build, execute and share cloud configuration, compliance, and security frameworks using SQL, HCL and a little elbow grease! We would love your help to expand the open source documentation and control coverage for CIS, PCI, HIPAA, NIST… and the best way to get started is to [join our new Slack workspace](https://steampipe.io/community/join) and raise your hand; we would love to talk to you!