# What's new in the CIS v1.5 benchmark for AWS
> Our analysis of the five new recommendations.
By Bob Tordella
Published: 2022-09-02
The [Center for Internet Security](https://www.cisecurity.org/) (CIS) just released an updated version (v1.5) of their CIS AWS Benchmark. The new version of the benchmark updates MITRE mappings, updates audit and remediation steps in accordance with AWS changes, and offers five new recommendations that we'll review here.
## Our take on the new recommendations
- **2.3.2 Ensure Auto Minor Version Upgrade feature is Enabled for RDS Instances** — This is a practical and easy way to make sure your database engines have all the new features, bug fixes, and security patches. If you do this work manually you'll inevitably fall behind. Automation is your friend.
- **2.3.3 Ensure that public access is not given to RDS Instances** — Most databases aren't meant to be accessible to the public. As a rule, assume your workloads are internal and make exceptions when public access is required. For RDS database instances, setting `Public Access` to `No` only provides one layer of protection. Another way to mitigate risk: ensure that proper VPC security groups are associated with the instance, and that the each instance resides in a subnet that only routes internally.
- **2.4.1 Ensure that encryption is enabled for EFS file systems** — Like other encryption controls, this one helps reduce the risk of a data breach via direct access to an EFS storage device. Given the physical controls within AWS data centers that's unlikely to happen. But it's free to enable encryption, and the performance cost is negligible. So why not turn it on?
- **4.16 Ensure AWS Security Hub is enabled** — Do you use a solution that collects security data from AWS accounts, services, and other third-party products? If so, you can skip this one and avoid paying for both Security Hub and related services such as AWS Config.
- **5.3 Ensure no security groups allow ingress from ::/0 to remote server administration ports** — Finally, IPv6 becomes a first-class citizen among CIS recommendations! This is the IPv6 version of "5.2 Ensure no security groups allow ingress from 0.0.0.0/0 to remote server administration ports."
## Try the new AWS CIS v1.5 controls!
The [Steampipe AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance), packed with hundreds of controls that check your AWS accounts for compliance with 21 benchmarks including CIS, PCI, HIPAA, SOC2, FedRAMP and more, now includes new controls for AWS CIS v1.5. If you're new to Steampipe, [download](https://steampipe.io/downloads) Steampipe, [install and configure](https://hub.steampipe.io/plugins/turbot/aws#get-started) the AWS plugin, and run these commands.
```
steampipe plugin update aws
git clone https://github.com/turbot/steampipe-mod-aws-compliance.git
cd steampipe-mod-aws-compliance
steampipe check benchmark.cis_v150
```
If you've already installed Steampipe and the AWS plugin, and cloned the AWS Compliance mod, then just do this.
```
cd steampipe-mod-aws-compliance
git pull
steampipe check benchmark.cis_v150
```
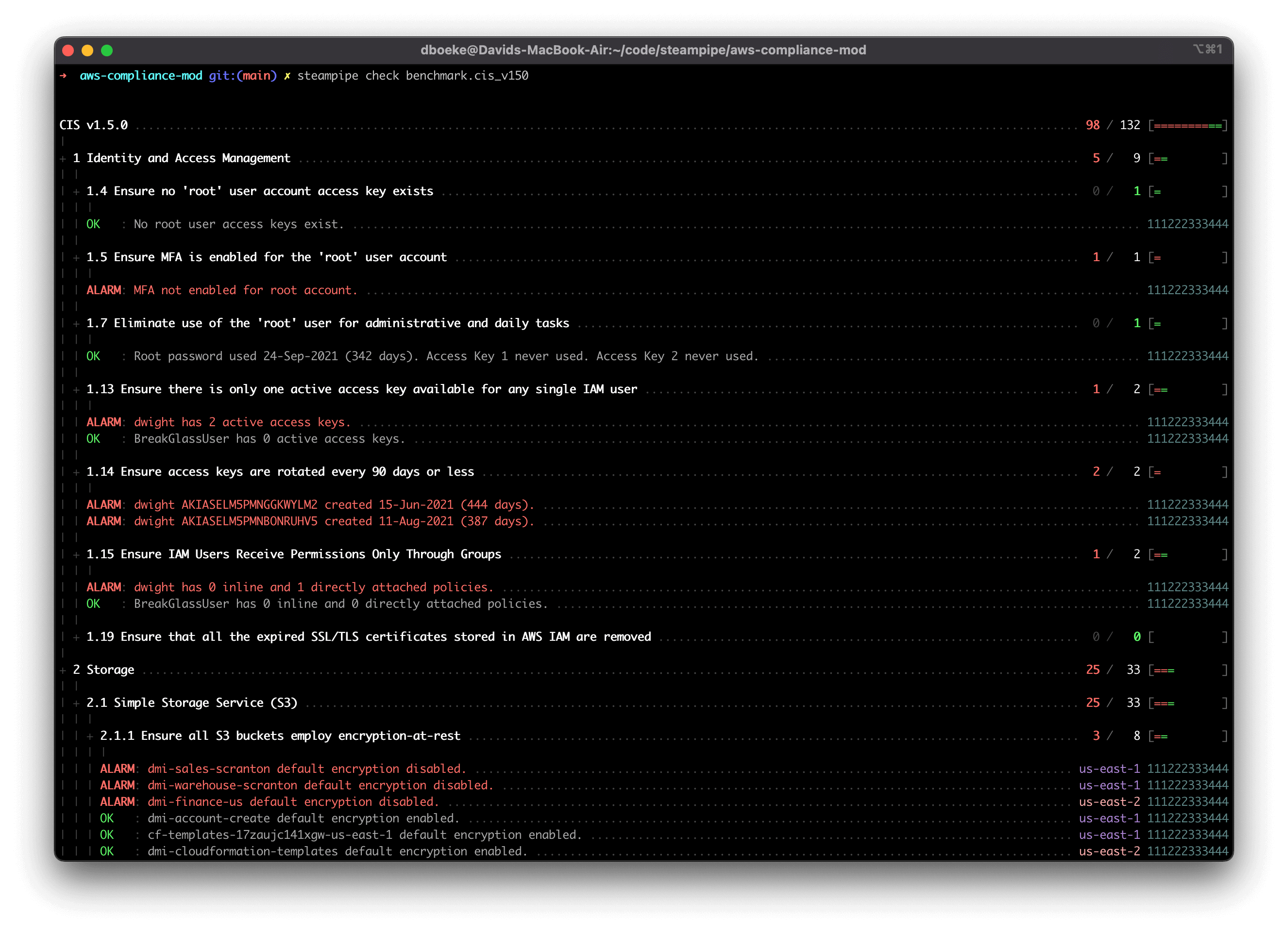
Here's a sample report in the console.
You can output results to formats including JSON, CSV, HTML, and ASFF, or use [custom output templates](https://steampipe.io/docs/develop/writing-control-output-templates) to create new output formats.
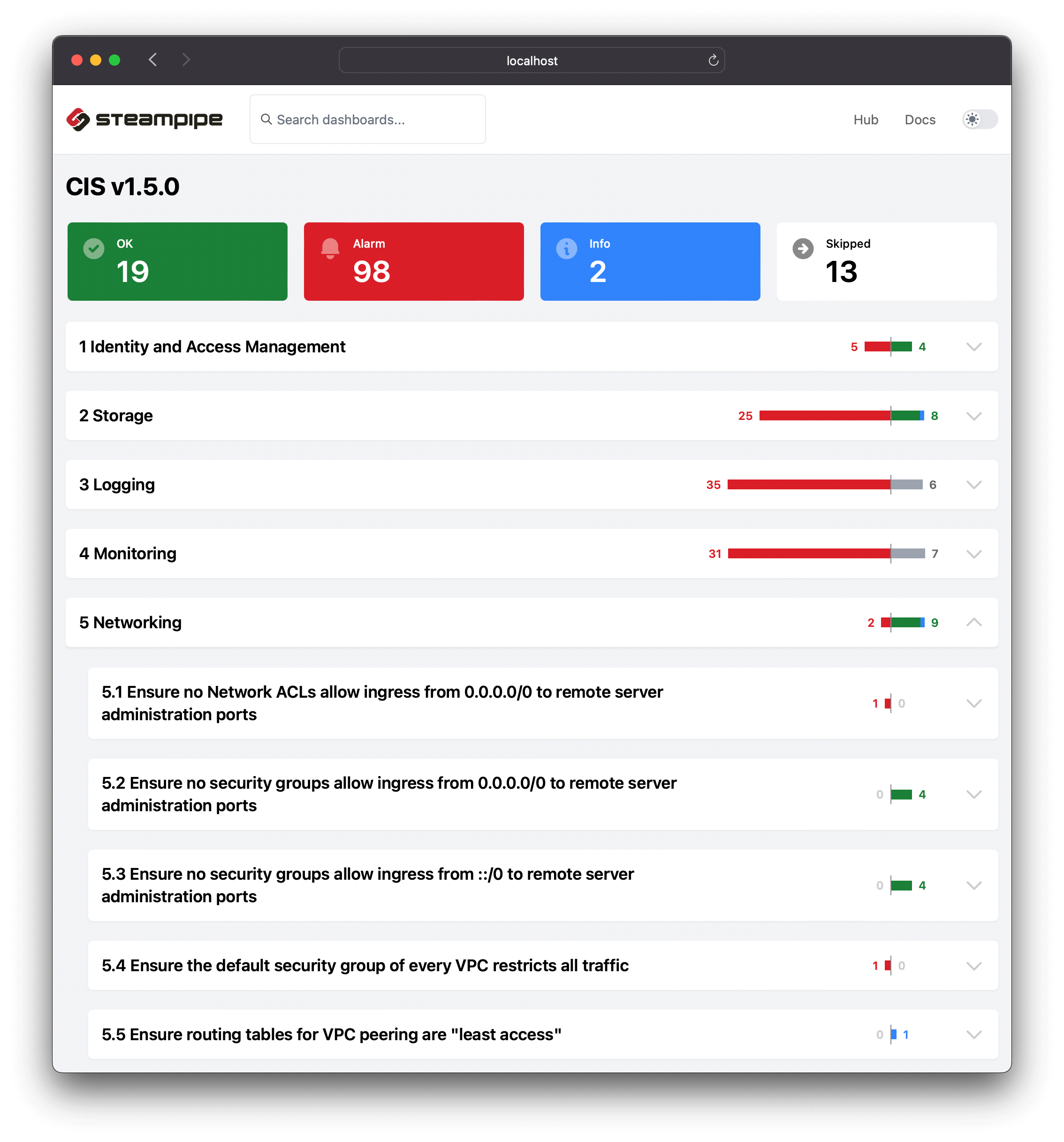
To view the AWS CIS v1.5 benchmark report in your browser, run this command in the same cloned repo.
```
steampipe dashboard
```
Then open `http://localhost:9194` in your browser and view the dashboard.
## We love open source!
Steampipe delivers a full suite of tools to build, execute and share cloud configuration, compliance, and security frameworks using HCL + SQL! We would love your help to expand the open source documentation and control coverage for CIS, PCI, HIPAA, NIST, and more. The best way to get started is to [join our Slack community](https://steampipe.io/community/join); we would love to talk to you!