# What's new in the CIS v1.5 benchmark for Azure
> Our analysis of the Azure recommendations.
By Chris Farris
Published: 2022-10-04
The [Center for Internet Security](https://www.cisecurity.org/) (CIS) just released an updated version (v1.5) of their CIS [Azure Foundations Benchmark](https://www.cisecurity.org/benchmark/azure). The new version of the benchmark updates MITRE mappings, along with audit and remediation
steps in accordance with Microsoft's changes. The Azure Benchmark weighs in at 555 pages and 147 different recommendations. Version 1.5 introduces 34 new or substantially updated recommendations. In this post we call out those that we consider to be most practical to implement, and most likely to reduce risk. You can see the full list of recommendations in the appendix below.
## Our take on the new recommendations
### Private endpoints
Private endpoints allow applications to access a service directly from a customer's VNet, without having to transit the public internet. To mitigate the risk of data loss due to misconfiguration, ensure that your data is only accessible from private networks. It's inexpensive to implement these three recommendations, and they deliver the most bang for the buck.
* 3.10 Ensure Private Endpoints are used to access Storage Accounts (Level 1)
* 4.5.2 [Cosmos DB] Ensure That Private Endpoints Are Used Where Possible (Level 2)
* 8.7 Ensure that Private Endpoints are Used for Azure Key Vault (Level 2)
### Azure perimeter
Four new recommendations address monitoring and managing your Azure perimeter. The first two ensure that alerts are generated when a public IP address is created, updated, or deleted. You cannot protect what you don't know exists. Your security team needs this information in your asset or IP address management (IPAM) system to properly defend the network.
The second two recommendations focus on ensuring that all public access to the environment is properly evaluated and governed.
These are all Level 1 recommendations: inexpensive, and low risk to implement.
* 5.2.9 Ensure that `Activity Log Alert` exists for `Create or Update Public IP Address` rule
* 5.2.10 Ensure that `Activity Log Alert` exists for `Delete Public IP Address` rule
* 6.4 Ensure that HTTP(S) access from the Internet is evaluated and restricted
* 6.7 Ensure that Public IP addresses are Evaluated on a Periodic Basis
### Mitigate account take-over risk
In Azure, anyone with Owner permission to a Subscription can remove that subscription from the company's AzureAD, or broadly change who has access to the subscription. This is a potential subscription take-over risk and should be disabled.
* 1.25 Ensure That `Subscription Entering AAD Directory` and `Subscription Leaving AAD Directory` Is Set To `Permit No One` (Level 2)
### Leverage conditional access
CIS released six new control recommendations for Azure AD's [Conditional Access capability](https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview). Conditional Access can help you build policies that require MFA, define the trusted subnets a request can come from, or define a country that a request must not originate from. In some cases, you can even define the security profile of the system that originates the request.
These settings require you to have a [premium Microsoft 365 or Azure AD plan](https://hub.steampipe.io/mods/turbot/azure_compliance/controls/benchmark.cis_v150_1_2?context=benchmark.cis_v150/benchmark.cis_v150_1#overview) so may not work for all organizations.
* 1.2.1 Ensure Trusted Locations Are Defined
* 1.2.2 Ensure that an exclusionary Geographic Access Policy is considered
* 1.2.3 Ensure that A Multi-factor Authentication Policy Exists for Administrative Groups
* 1.2.4 Ensure that A Multi-factor Authentication Policy Exists for All Users
* 1.2.5 Ensure Multi-factor Authentication is Required for Risky Sign-ins
* 1.2.6 Ensure Multi-factor Authentication is Required for Azure Management
### Enable Microsoft Defender
CIS introduced six new recommendations to enable Microsoft Defender (formerly Azure Security Center) on newly-supported Azure services. Microsoft Defender is [an added cost](https://azure.microsoft.com/en-us/pricing/details/defender-for-cloud/), and may not be appropriate for everyone. But if you've operationalized Microsoft Defender in your security program, and are using any of these services, enabling protection is a no-brainer.
* 2.1.3 Ensure That `Microsoft Defender for Databases` Is Set To `On`
* 2.1.6 Ensure That `Microsoft Defender for Open-Source Relational Databases` Is Set To `On`
* 2.1.9 Ensure That `Microsoft Defender for Cosmos DB` Is Set To `On`
* 2.1.11 Ensure That `Microsoft Defender for DNS` Is Set To `On`
* 2.1.12 Ensure That `Microsoft Defender for IoT` Is Set To `On`
* 2.1.13 Ensure That `Microsoft Defender for Resource Manager` Is Set To `On`
## Evaluate your environment with Azure CIS v1.5
The [Steampipe Azure Compliance mod](https://hub.steampipe.io/mods/turbot/azure_compliance), packed with hundreds of controls that check your Azure subscriptions for compliance with the CIS Benchmarks, HIPAA HITRUST, NIST, and more, now includes new controls for Azure CIS v1.5. If you're new to Steampipe, [download](https://steampipe.io/downloads) Steampipe, then install and configure the [Steampipe Azure plugin](https://hub.steampipe.io/mods/turbot/azure_compliance#installation), then run these commands.
```bash
steampipe plugin update azure
git clone https://github.com/turbot/steampipe-mod-azure-compliance.git
cd steampipe-mod-azure-compliance
steampipe check benchmark.cis_v150
```
If you've already installed Steampipe and the Azure plugin, and cloned the Azure Compliance mod, then just do this.
```bash
cd steampipe-mod-azure-compliance
git pull
steampipe check benchmark.cis_v150
```
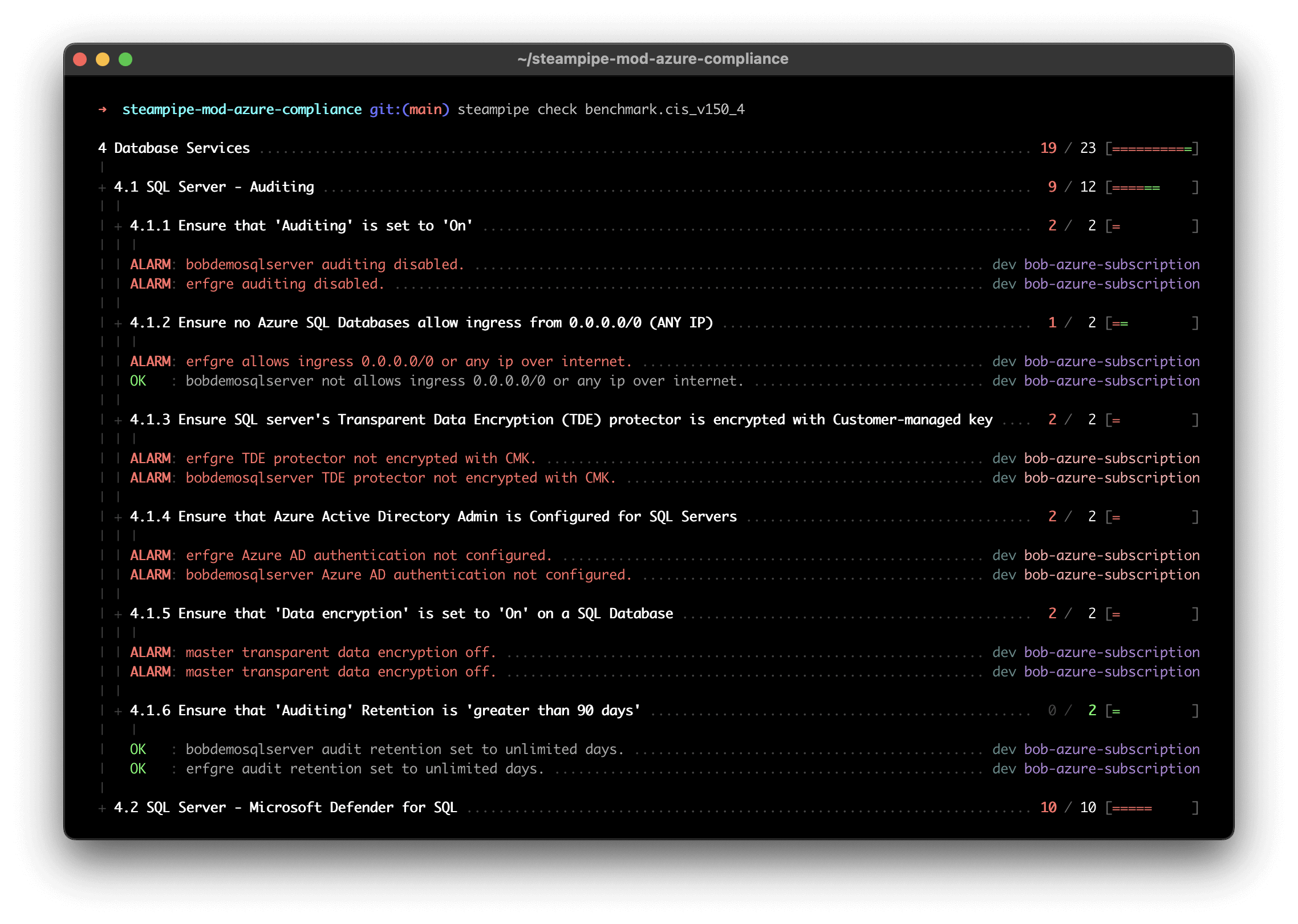
Here's a sample report in the console.
You can output results to formats including JSON, CSV, HTML, or use [custom output templates](https://steampipe.io/docs/develop/writing-control-output-templates) to create new output formats.
To view the Azure CIS v1.5 benchmark report in your browser, run this command in the same cloned repo.
```bash
steampipe dashboard
```
Then open `http://localhost:9194` in your browser and view the dashboard.
## We love open source!
Steampipe delivers a full suite of tools to build, execute and share cloud configuration, compliance, and security frameworks using HCL + SQL! We would love your help to expand the open source documentation and control coverage for CIS, PCI, HIPAA, NIST, and more. The best way to get started is to [join our Slack community](https://steampipe.io/community/join); we would love to talk to you!
## Appendix: All new (or substantially updated) CIS v1.5 recommendations for Azure
* 1.2 Conditional Access
* 1.2.1 Ensure Trusted Locations Are Defined
* 1.2.2 Ensure that an exclusionary Geographic Access Policy is considered
* 1.2.3 Ensure that A Multi-factor Authentication Policy Exists for Administrative Groups
* 1.2.4 Ensure that A Multi-factor Authentication Policy Exists for All Users
* 1.2.5 Ensure Multi-factor Authentication is Required for Risky Sign-ins
* 1.2.6 Ensure Multi-factor Authentication is Required for Azure Management
* 1.3 Ensure Access Review is Set Up for External Users in Azure AD Privileged Identity Management (Level 2)
* 1.5 Ensure that 'Allow users to remember multi-factor authentication on devices they trust' is 'Disabled' (Level 1)
* 1.7 Ensure that a Custom Bad Password List is set to 'Enforce' for your Organization (Level 1)
* 1.11 Ensure That ‘Users Can Consent to Apps Accessing Company Data on Their Behalf’ Is Set To ‘Allow for Verified Publishers’ (Level2)
* 1.25 Ensure That ‘Subscription Entering AAD Directory’ and ‘Subscription Leaving AAD Directory’ Is Set To ‘Permit No One’ (Level 2)
* 2.1 Microsoft Defender Plans
* 2.1.3 Ensure That Microsoft Defender for Databases Is Set To 'On'
* 2.1.6 Ensure That Microsoft Defender for Open-Source Relational Databases Is Set To 'On'
* 2.1.9 Ensure That Microsoft Defender for Cosmos DB Is Set To 'On'
* 2.1.11 Ensure That Microsoft Defender for DNS Is Set To 'On'
* 2.1.12 Ensure That Microsoft Defender for IoT Is Set To 'On'
* 2.1.13 Ensure That Microsoft Defender for Resource Manager Is Set To 'On'
* 2.2.2 Ensure that Auto provisioning of 'Vulnerability assessment for machines' is Set to 'On' (Level 2) - This requires additional licensing and could duplicate existing vulnerability management solutions.
* 2.2.3 Ensure that Auto provisioning of 'Microsoft Defender for Containers components' is Set to 'On' (Level 2) - This recommendation, which only applies if the organization has enabled Microsoft Defender for Containers, ensures that the container hosts have the required agents. If you’re planning to deploy Defender, ensuring full coverage is critical.
* 3.2 Ensure that ‘Enable Infrastructure Encryption’ for Each Storage Account in Azure Storage is Set to ‘enabled’ (Level 2)
* 3.3 Ensure that 'Enable key rotation reminders' is enabled for each Storage Account (Level 1)
* 3.10 Ensure Private Endpoints are used to access Storage Accounts (Level 1)
* 4.5.1 Ensure That 'Firewalls & Networks' Is Limited to Use Selected Networks Instead of All Networks (Level 2)
* 4.5.2 [Cosmos DB] Ensure That Private Endpoints Are Used Where Possible (Level 2)
* 4.4.3 Ensure server parameter 'audit_log_enabled' is set to 'ON' for MySQL Database Server (Level 2)
* 4.4.4 Ensure server parameter 'audit_log_events' has 'CONNECTION' set for MySQL Database Server (Level 2)
* 5.1.7 Ensure that logging for Azure AppService 'AppServiceHTTPLogs' is enabled. (Level 2)
* 5.2.9 Ensure that Activity Log Alert exists for Create or Update Public IP Address rule (Level 1)
* 5.2.10 Ensure that Activity Log Alert exists for Delete Public IP Address rule (Level 1)
* 6.4 Ensure that HTTP(S) access from the Internet is evaluated and restricted (Level 1)
* 6.7 Ensure that Public IP addresses are Evaluated on a Periodic Basis (Level 1)
* 8.6 Enable Role Based Access Control for Azure Key Vault (Level 2)
* 8.7 Ensure that Private Endpoints are Used for Azure Key Vault (Level 2)
* 8.8 Ensure Automatic Key Rotation is Enabled Within Azure Key Vault for the Supported Services (Level 2)