# What's new in the CIS v2.0 benchmark for AWS
> Our analysis of the latest CIS AWS recommendations.
By Rahul Srivastav
Published: 2023-07-07
The [Center for Internet Security](https://www.cisecurity.org/) (CIS) just released an updated version (v2.0) of their CIS AWS Benchmark. The new version of the benchmark includes 2 new recommendations, 1 removed, and updates to descriptions and remediation steps.
## Our take on the latest major changes
- **Added - 1.22 Ensure access to AWSCloudShellFullAccess is restricted:** AWS CloudShell allows running CLI commands with full access, including file upload/download and sudo permissions. This presents a potential data exfiltration channel for malicious cloud admins. Restricting access and denying file transfer permissions through a more restrictive IAM policy is recommended. Personally, CloudShell is a great way to run commands in your account quickly and [quickly enable tools like Steampipe](https://dev.to/aws-builders/instantly-query-aws-with-sql-in-cloudshell-hd0). However, with any highly privileged role, boundary and lockdown permissions should be considered for the least privilege restrictions.
- **Added - 5.6 Ensure that EC2 Metadata Service only allows IMDSv2:** — Instance Metadata Service Version 2 (IMDSv2), which is a session-oriented method which provides temporary, frequently rotated credentials. Version 2 adds new protections to mitigate vulnerabilities from open website application firewalls, open reverse proxies, SSRF, etc. This is a common recommendation used across many other [frameworks](https://hub.steampipe.io/mods/turbot/aws_compliance/controls/control.ec2_instance_uses_imdsv2) like NIST, FedRamp, and HIPAA.
- **Removed - 2.1.1 Ensure all S3 buckets employ encryption-at-rest:** — In Benchmark v1.5, the requirement for encryption-at-rest in S3 buckets (2.1.1) was removed since AWS now automatically encrypts all new objects using SSE-S3 as the default encryption setting since January 2023. Existing buckets with S3 Default Encryption remain unchanged, so you may want to still check for encryption-at-rest for legacy buckets. However, moving forward at a minimum all new buckets will be encrypted and you cannot remove encryption any longer. With the removal of the control, all other Storage recommendations have changed their IDs in section 2.0.
## Try the new AWS CIS v2.0 controls!
The [Steampipe AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance), is packed with hundreds of controls that check your AWS accounts for compliance with 25 benchmarks including NIST, PCI, HIPAA, SOC2, FedRAMP and more, now includes new controls for AWS CIS v2.0. If you're new to Steampipe, [download](https://steampipe.io/downloads) Steampipe, [install and configure](https://hub.steampipe.io/plugins/turbot/aws#get-started) the AWS plugin, and run these commands.
```
steampipe plugin update aws
git clone https://github.com/turbot/steampipe-mod-aws-compliance.git
cd steampipe-mod-aws-compliance
steampipe check aws_compliance.benchmark.cis_v200
```
If you've already installed Steampipe and the AWS plugin, and cloned the AWS Compliance mod, then just do this.
```
cd steampipe-mod-aws-compliance
git pull
steampipe check aws_compliance.benchmark.cis_v200
```
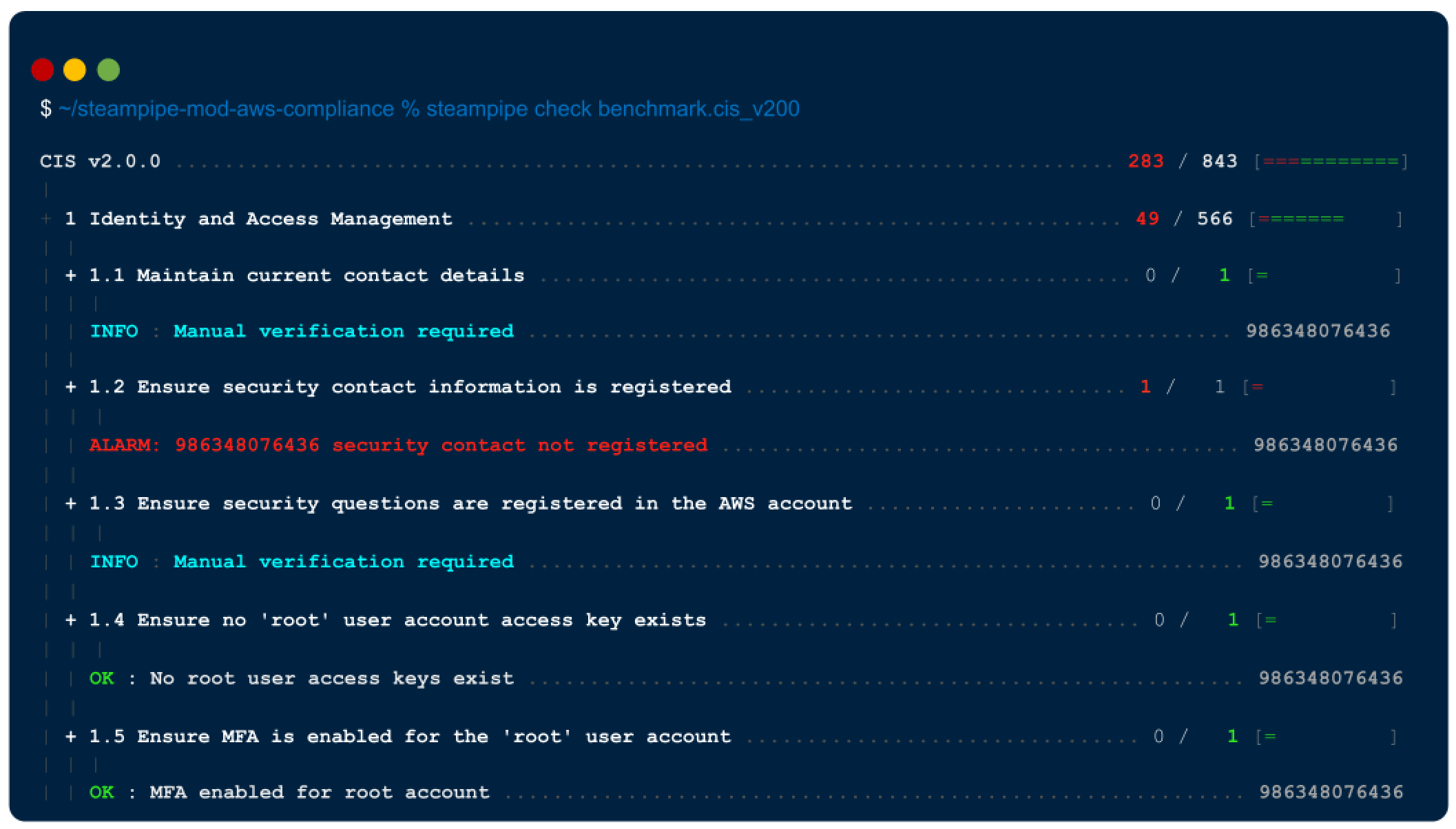
Here's a sample report in the console.
You can output results to formats including JSON, CSV, HTML, and ASFF, or use [custom output templates](https://steampipe.io/docs/develop/writing-control-output-templates) to create new output formats.
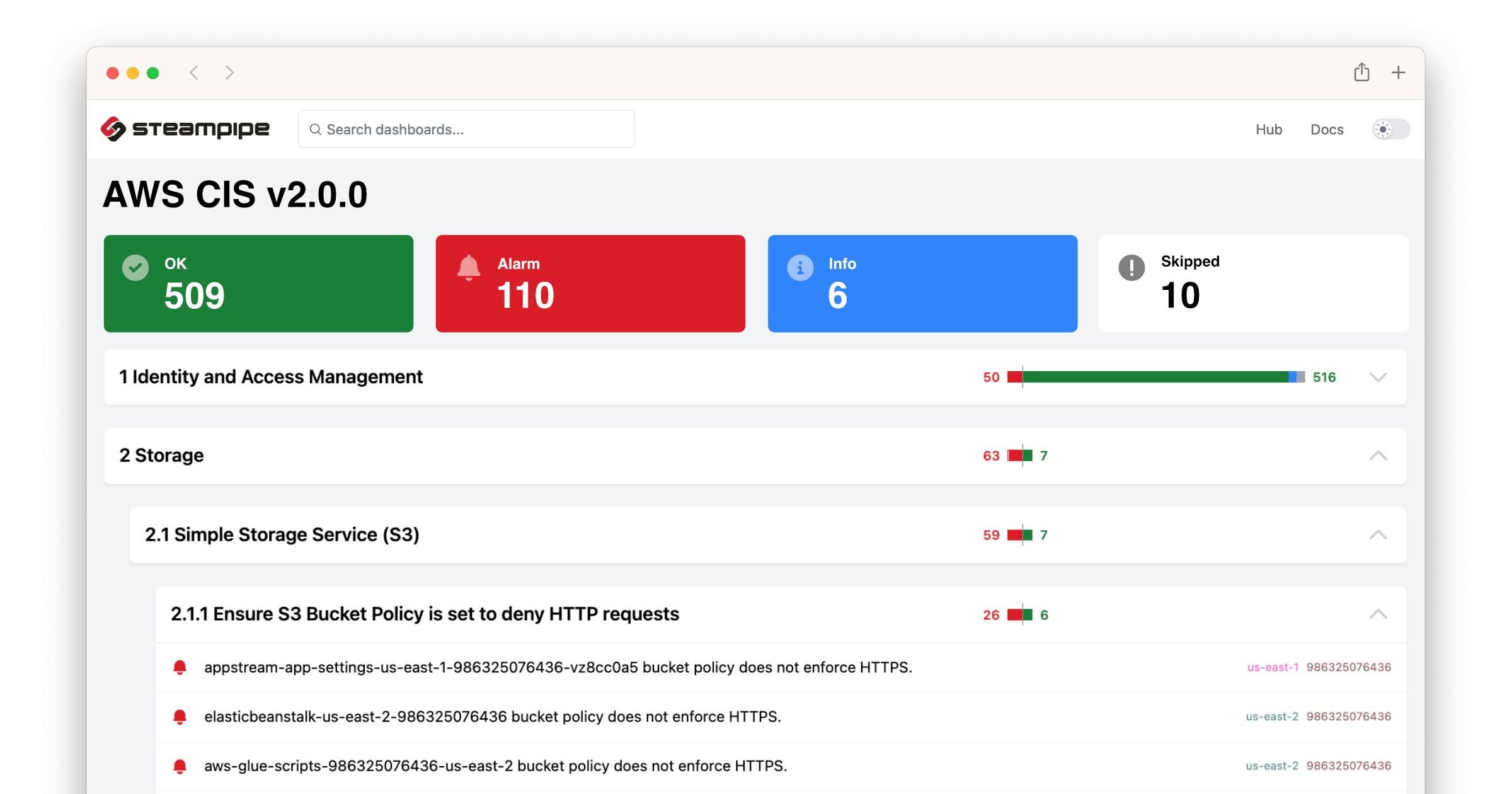
To view the AWS CIS v2.0 benchmark report in your browser, run this command in the same cloned repo.
```
steampipe dashboard
```
Then open `http://localhost:9194` in your browser and view the dashboard.
## We love open source!
Steampipe delivers a full suite of tools to build, execute and share cloud configuration, compliance, and security frameworks using HCL + SQL! We would love your help to expand the open source documentation and control coverage for CIS, PCI, HIPAA, NIST, and more. The best way to get started is to [join our Slack community](https://steampipe.io/community/join); we would love to talk to you!