# What's new in the CIS v3.0 benchmark for AWS
> Our analysis of the latest CIS AWS recommendations.
By Bob Tordella
Published: 2024-02-08
The [Center for Internet Security](https://cisecurity.org) (CIS) just released an updated version (v3.0) of their CIS AWS Benchmark. The new version of the benchmark removes 2 recommendations, updates MITRE mappings, and improves 20 recommendations' descriptions & remediation steps.
## Our take on the latest major changes
- **Removed - 3.3 Ensure the S3 bucket used to store CloudTrail logs is not publicly accessible:**
This recommendation is redundant to the existing [2.1.4 Ensure that S3 Buckets are configured with 'Block public access (bucket settings)'](https://hub.steampipe.io/mods/turbot/aws_compliance/controls/control.cis_v300_2_1_4?context=benchmark.cis_v300/benchmark.cis_v300_2/benchmark.cis_v300_2_1) control which already covers a recommendation to enable S3 block public access settings based on data sensitivity, least privilege, and use case.
- **Removed - 3.4 Ensure CloudTrail trails are integrated with CloudWatch Logs:** —
The original intent for this recommendation was to ensure AWS account activity is being captured, monitored, and appropriately alarmed on. CloudWatch Logs is a native way to accomplish this, but you could also consider logging to AWS S3 which a SIEM tool like [Splunk](https://splunk.com) can collect logs from those S3 buckets. Also, this recommendation overlaps with the Monitoring section which was once very specific on using CloudWatch logs to filter and alert on issues. Overtime the Monitoring section has evolved to recognize other native solutions like [AWS Security Hub](https://aws.amazon.com/security-hub/), or the use of CSPM and CNAPP alternatives such as [Turbot Guardrails](https://turbot.com/guardrails) which provides real-time monitoring of AWS API events and instantly actions guardrails to correct misconfigurations.
Note: the removal of these two recommendations changes the numbering scheme from the AWS CIS v2.0 benchmark. e.g. what was once [3.5 Ensure AWS Config is enabled in all regions](https://hub.steampipe.io/mods/turbot/aws_compliance/controls/control.cis_v200_3_5?context=benchmark.cis_v200/benchmark.cis_v200_3) is now [3.3 Ensure AWS Config is enabled in all regions](https://hub.steampipe.io/mods/turbot/aws_compliance/controls/control.cis_v300_3_3?context=benchmark.cis_v300/benchmark.cis_v300_3).
## Try the new AWS CIS v3.0 controls!
The [Steampipe AWS Compliance mod](https://github.com/turbot/steampipe-mod-aws-compliance), is packed with hundreds of controls that check your AWS accounts for compliance with 25+ benchmarks including NIST, PCI, HIPAA, SOC2, FedRAMP and more, now includes new controls for AWS CIS v3.0. If you're new to Steampipe, [download](https://steampipe.io/downloads) Steampipe, [install and configure](https://hub.steampipe.io/plugins/turbot/aws#get-started) the AWS plugin, and run these commands.
```
steampipe plugin update aws
git clone https://github.com/turbot/steampipe-mod-aws-compliance.git
cd steampipe-mod-aws-compliance
steampipe check aws_compliance.benchmark.cis_v300
```
If you've already installed Steampipe and the AWS plugin, and cloned the AWS Compliance mod, then just do this.
```
cd steampipe-mod-aws-compliance
git pull
steampipe check aws_compliance.benchmark.cis_v300
```
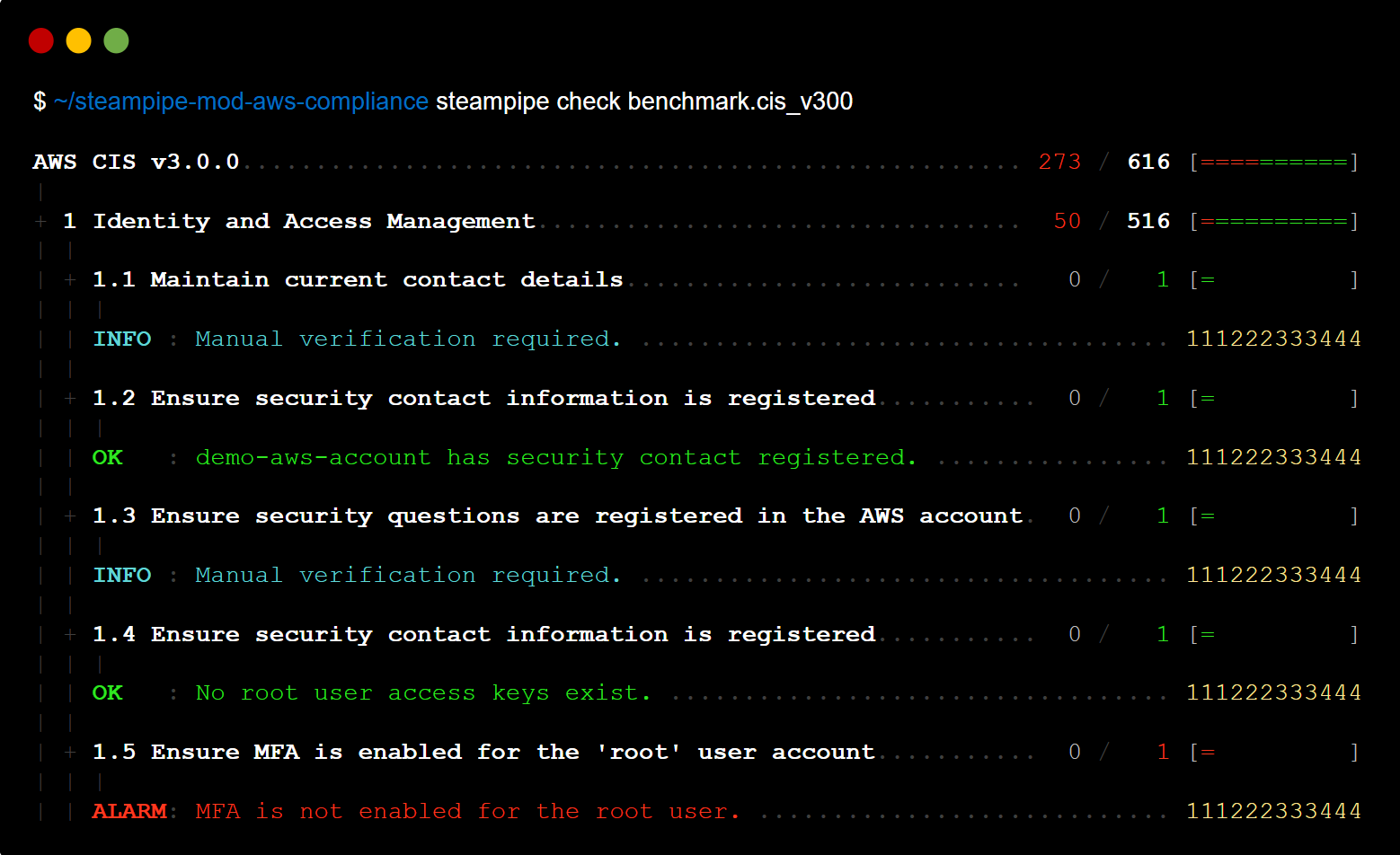
Here's a sample report in the console.
You can output results to formats including JSON, CSV, HTML, and ASFF, or use [custom output templates](https://steampipe.io/docs/develop/writing-control-output-templates) to create new output formats.
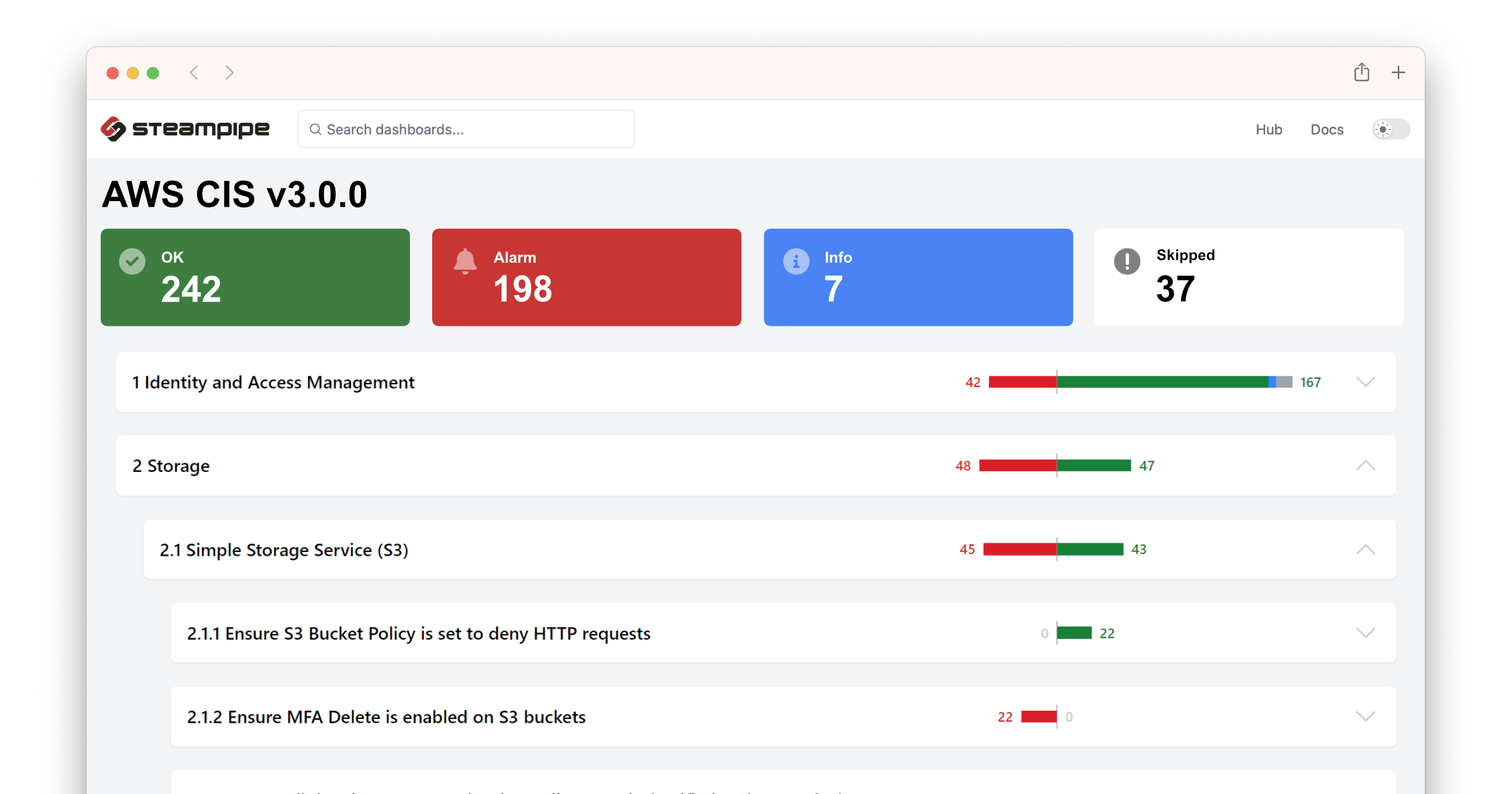
To view the AWS CIS v3.0 benchmark report in your browser, run this command in the same cloned repo.
```
steampipe dashboard
```
Then open `http://localhost:9194` in your browser and view the dashboard.
## Cloud intelligence for your AWS accounts
Steampipe also includes 200+ ready-to-use [AWS cloud intelligence dashboards](https://hub.steampipe.io/mods?q=aws) to gain insights, assess your cloud inventory, navigate resource relationships, evaluate cost optimization recommendations and ensure security posture best practices.
Getting started with Steampipe? Let us know how you go by sending a message in the #steampipe channel of our [Slack community](https://turbot.com/community/join).