# Uncovering Attack Paths with Cloud Resource Graphs
> Leveraging Steampipe's Relationship Graphs for Penetration Testing in GCP
By Chris Farris
Published: 2023-03-03
In 2015, John Lambert at Microsoft coined the term “Defenders think in lists. Attackers think in graphs”. His reasoning is that defenders, driven by governance, risk, and compliance, compile lists of assets and then attempt to protect them. On the other hand, attackers don’t have the privilege of knowing everything in their target environment. Instead, they find a foot-hold, then look to see where they can pivot. Depending on the attacker’s motivation, they may not even know where or how to obtain their objective.
As a penetration tester, you’re usually given a limited time for an engagement and limited access to see the environment. So while you could run a scanner and enumerate all the vulnerabilities and configuration issues, you also have the opportunity to map out the attack graphs. Steampipe’s new relationship graphs can help visualize this.
## Mapping an attack path through GCP
Let's start with a simple GCP-hosted application, a statically hosted WordPress site. You can trace the relationships between the cloud resources using your limited read access to the GCP project.
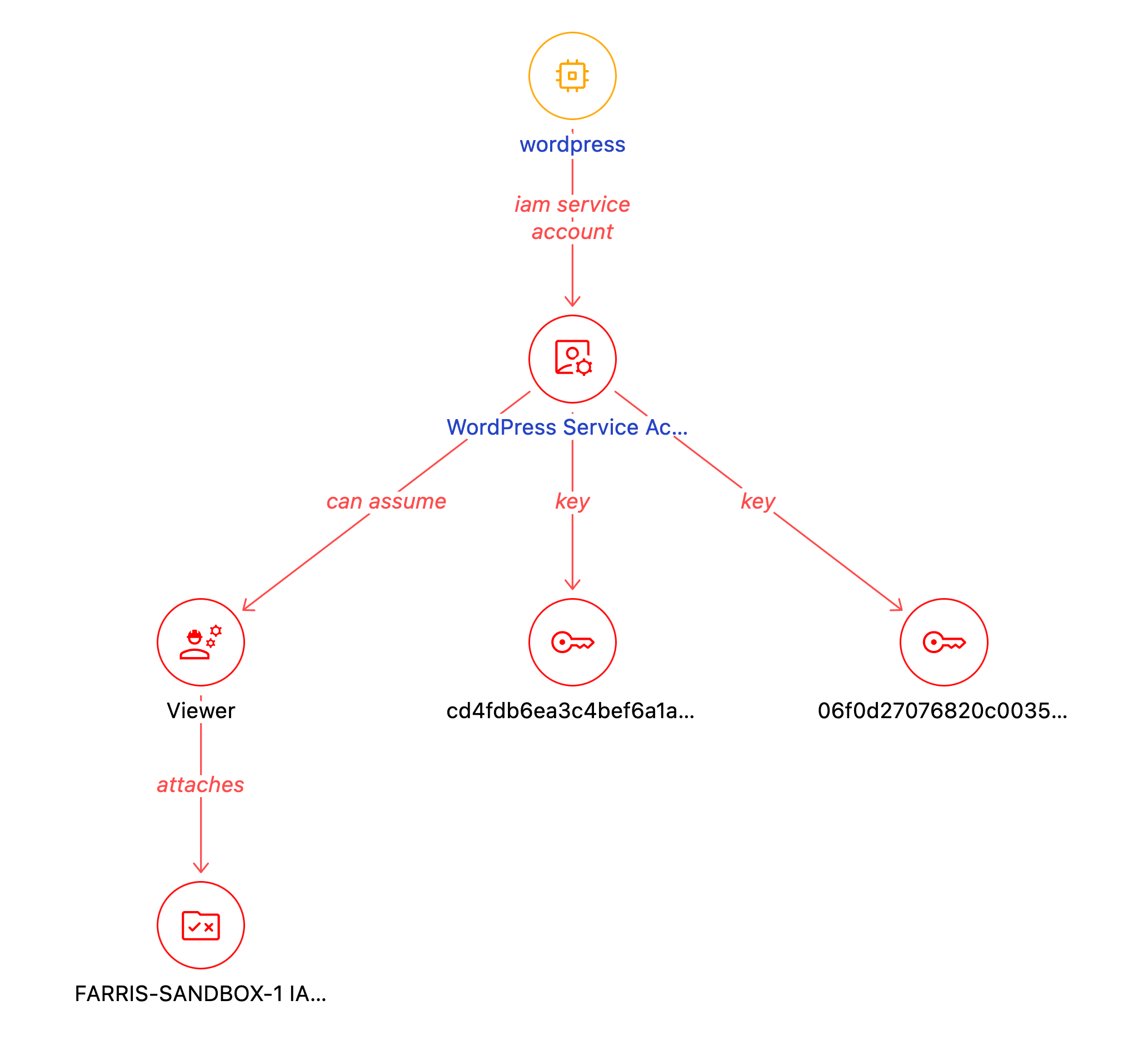
As an attacker, you’d typically start with an internet-exposed resource. For this example, we’ll start with the WordPress instance:

We see the instance has a single drive, two security groups, and a service account. The machine is in the `dev-vpc`. The first thing you’d want to do is see what other resources that VM has access to. So we can pivot to the [service account](https://cloud.google.com/iam/docs/service-accounts) and observe the keys and the excessive permission (Viewer).
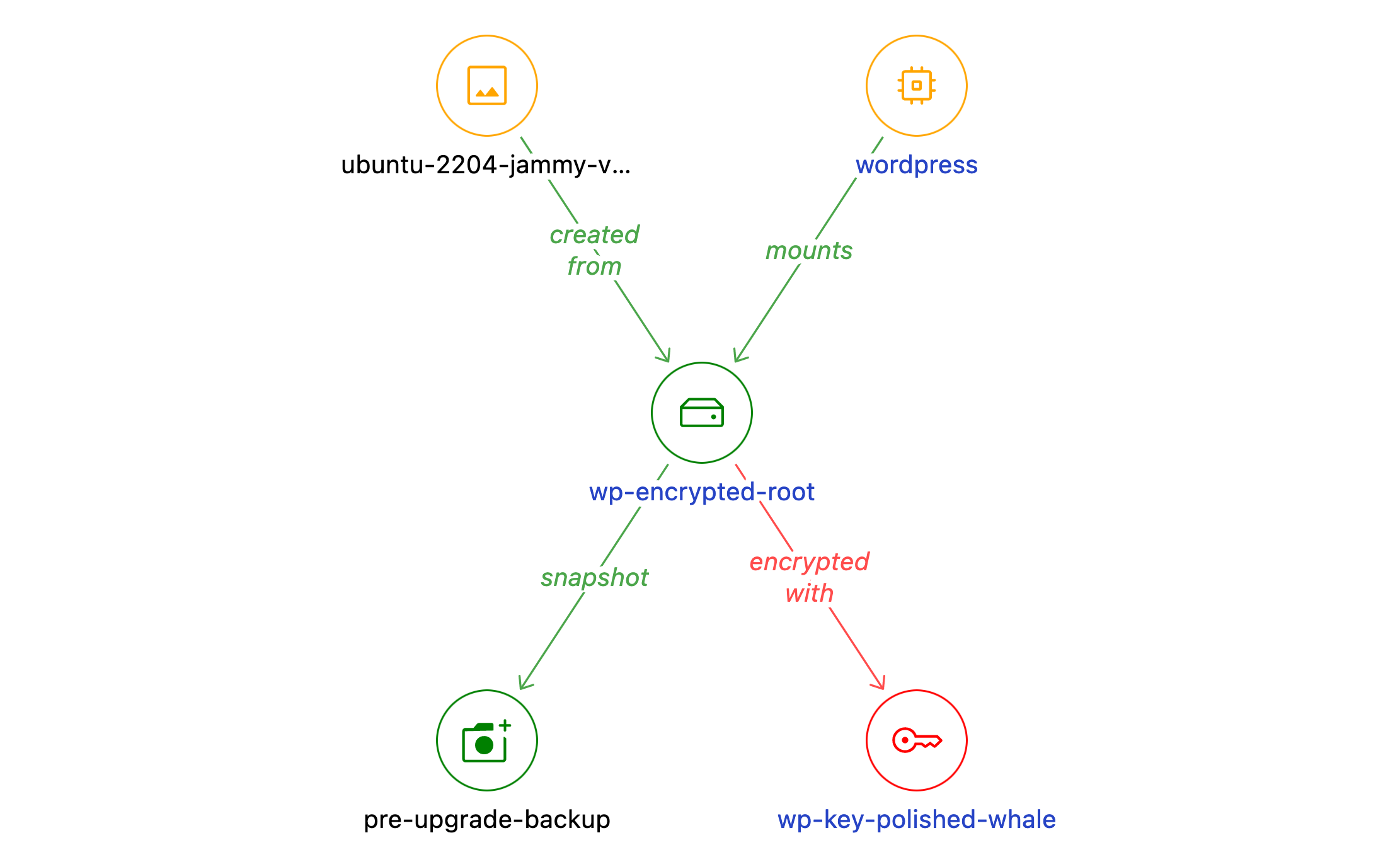
Looking at the disk, we get a few more critical bits of information. Our target has used the latest Ubuntu, which might make our job harder. They also have snapshots enabled, which gives them a potential recovery path in the case of a ransomware attack.
If you return to the GCP Compute Instance Detail page, you can click on the VPC to see what else is there.

From this VPC view, you can see there is a Database in the network. Click on that for more information about the backups and databases inside.

## Defenders need to understand graphs but need to think in lists
John Lambert’s essay was a call to action for defenders to start thinking in graphs. While there is value in understanding an attacker’s mindset, the counterargument for defenders thinking in graphs is the [defender’s dilemma](https://www.rand.org/pubs/research_reports/RR1024.html). Defenders have to be right every time. Attackers have to be lucky once. To ensure you’re securing 100% of your assets, you must find and protect 100% of your assets. Steampipe can find all our cloud assets across your entire configured environment using its extensive list of [plugins](https://hub.steampipe.io/plugins) and [mods](https://hub.steampipe.io/mods).
For defenders, leveraging these relationship graphs can help uncover unexpected relationships. In addition, they can help defenders explain and articulate cloud security risks to their development and operations partners.
## Go and discover your cloud!
Whether you're using lists or graphs, it's imperative to know what you have to manage and secure it properly. The Steampipe ecosystem now offers over a hundred plugins; each provides several, dozens, or even hundreds of tables. You can discover resources in [AWS](https://hub.steampipe.io/plugins/turbot/aws), [Azure](https://hub.steampipe.io/plugins/turbot/azure), [Alibaba Cloud](https://hub.steampipe.io/plugins/turbot/alicloud), [Oracle Cloud](https://hub.steampipe.io/plugins/turbot/oci), [GitHub](https://hub.steampipe.io/plugins/turbot/github), [Kubernetes](https://hub.steampipe.io/plugins/turbot/kubernetes), [DigitalOcean](https://hub.steampipe.io/plugins/turbot/digitalocean), [Equinix](https://hub.steampipe.io/plugins/turbot/equinix), [Hetzner](https://hub.steampipe.io/plugins/turbot/hcloud), and [numerous others](https://hub.steampipe.io/plugins).
The sky's the limit, and we look forward to hearing about your discoveries in our [Slack community](https://turbot.com/community/join).