# AWS pre:Invent 2022
> We highlight AWS's interesting and impactful security announcements in the lead-up to AWS re:Invent.
By Chris Farris
Published: 2022-11-23
It's once again Thanksgiving week, which means I'm again catching up on all the [AWS announcements](https://aws.amazon.com/about-aws/whats-new/2022/) from the last 30 days, so I can decide who to bother at re:Invent with dumb questions or snarky suggestions.
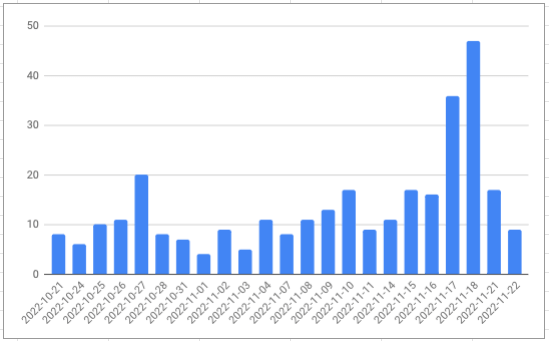
There were 240 announcements in November (up from 234 last year). Again is the break down of number of announcements by day since October 21st:
It's pretty clear that AWS Service Teams rush to get their stuff launched at the last minute. The 310 announcements in the 31 days leading up to re:Invent account for 18% of the 1754 announcements so far in 2022.
(An aside: [last year's post](https://www.chrisfarris.com/post/preinvent2021/) was generated by parsing the HTML, this year, AWS has helpfully provided a [JSON feed](https://aws.amazon.com/api/dirs/items/search?item.directoryId=whats-new&sort_by=item.additionalFields.postDateTime&sort_order=desc&size={}&item.locale=en_US&tags.id=whats-new%23year%232022) of their announcements. )
Let's dive into the ones that security practitioners should be somewhat aware of.
## General things of interest
### [Announcing dark mode support in the AWS Management Console](https://aws.amazon.com/about-aws/whats-new/2022/10/dark-mode-support-aws-management-console/)
Announced On: 2022-10-21
> Today, we are excited to launch dark mode as a beta feature in the AWS Management Console. Dark mode is available as a setting for visual mode in Unified Settings. The setting persists for customers across browsers and devices.
Since the ancient Sumerians, scientists and philosophers have debated the formal start of pre:Invent. This year it made sense that the introduction of Dark Mode in the AWS console would commence the start of pre:Invent 2022. With dark mode, hackers can officially start using AWS for nefarious purposes, and this should serve as a warning to all the defenders: The Cloud is finally a target.
### Three new AWS Regions!
* [A New AWS Region Opens in Switzerland](https://aws.amazon.com/blogs/aws/a-new-aws-region-opens-in-switzerland/) (2022-11-08)
* [Now Open–AWS Region in Spain](https://aws.amazon.com/blogs/aws/now-open-aws-region-in-spain) (2022-11-15)
* [Now Open the 30th AWS Region – Asia Pacific (Hyderabad) Region in India](https://aws.amazon.com/blogs/aws/now-open-the-30th-aws-region-asia-pacific-hyderabad-region-in-india/) (2022-11-21)
> [They are] pleased to announce the opening of our 28th AWS Region: Europe (Zurich), also known by its API name: eu-central-2.
> The AWS Region in Aragón, Spain, is now open. The official name is Europe (Spain), and the API name is eu-south-2. You can start using it today to deploy workloads and store your data in Spain.
> Today we are announcing the general availability of the 30th AWS Region, Asia Pacific (Hyderabad) Region, with three Availability Zones and the ap-south-2 API name.
Thankfully, new regions no longer create a window of blindness while security teams spin up their controls. However, if your security or governance program doesn't implement an SCP that prevents `account:EnableRegion`, you probably should check to ensure no one has enabled these regions. As of this post, [GuardDuty is not yet available in either Hyderabad, Spain or Zurich](https://docs.aws.amazon.com/general/latest/gr/guardduty.html). I plan to personally inspect both eu-south-2 and eu-central-2 this summer, and will report back my findings.
### [Announcing AWS Resource Explorer](https://aws.amazon.com/about-aws/whats-new/2022/11/announcing-aws-resource-explorer/)
Announced On: 2022-11-08
> Today, AWS announces AWS Resource Explorer, a managed capability that simplifies the search and discovery of resources, such as Amazon Elastic Compute Cloud (Amazon EC2) instances, Amazon Kinesis streams, and Amazon DynamoDB tables, across AWS Regions in your AWS account. AWS Resource Explorer is available at no additional charge to you.
I already did a write-up of [Resource Explorer](https://steampipe.io/blog/resource-explorer). It will be more useful when it can support AWS Organizations.
## AWS Organizations & governance related announcements
### [AWS Organizations console now allows users to centrally manage primary contact information on AWS accounts](https://aws.amazon.com/about-aws/whats-new/2022/10/aws-organizations-console-centrally-manage-primary-contact-information-aws-accounts/)
Announced On: 2022-10-25
> Today, we are enhancing the AWS Organizations console to enable you to centrally view and update the primary contact information for your AWS accounts. This follows the release of the Primary Contact Information API that enabled you to programmatically manage primary contact information for accounts in your organization. With this launch, you can now also use the console to easily perform this operation without logging into each account separately. We already launched API and Organizations console support for alternate contacts, and support for additional account settings will be available in future releases.
For at least the past three re:Invents, [Steve Schmidt](https://youtu.be/oam8FDNJhbE?t=575) has had "Accurate Account Info" and "Update your Account Contacts" in his top-ten list of things you should be doing. Being able to do this in one place, without logging in as root, makes Steve's advice actionable.
### [Introducing the AWS Control Tower delivery and AWS Control Tower ready program](https://aws.amazon.com/about-aws/whats-new/2022/10/aws-control-tower-delivery-control-tower-ready-program/)
Announced On: 2022-10-27
> AWS Control Tower provides the easiest way to set up and govern a secure, multi-account AWS environment, and reduces the complexity and time required to establish governance supporting multiple AWS accounts. We are excited to introduce AWS Control Tower Delivery Partners offering consulting services on AWS Control Tower, and AWS Control Tower Ready Partners offering software products that support AWS Control Tower. AWS Control Tower Partners receive prescriptive guidance to build solutions on Control Tower, and their offerings are vetted by AWS Solutions Architects.
"Control Tower is so easy it requires an ecosystem of partners to help you implement it" perhaps isn't the messaging AWS intended.
### [AWS Control Tower now displays compliance status of external AWS Config rules](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-control-tower-displays-compliance-status-external-config-rules/)
Announced On: 2022-11-22
> AWS Control Tower now displays the compliance status of AWS Config rules deployed outside of AWS Control Tower. This view provides you with visibility into the compliance status of externally applied AWS Config rules in addition to AWS Config rules set up by AWS Control Tower.
As much as a pick on Control Tower, they are making improvements and moving beyond the "Control Tower only supports doing X, so therefore all customers should only do X" mentality. Control Tower probably merits another look sometime early next year.
### [Manage your resources from AWS Organizations using AWS CloudFormation](https://aws.amazon.com/about-aws/whats-new/2022/11/manage-resources-aws-organizations-cloudformation/)
Announced On: 2022-11-18
> AWS Organizations now supports AWS CloudFormation, allowing customers to manage accounts, organizational units (OUs), and policies within their organization using CloudFormation templates. With this latest integration, customers can efficiently deploy multiple organizational elements in a stack, allowing them to more easily scale across accounts with organization policies in place.
This has been a gap in AWS Organizations for a while. Tools like [org-formation](https://github.com/org-formation/org-formation-cli) were ok stop-gap solutions, but we needed an AWS native solution. Sadly, the current offering [doesn't really meet the use cases I have for managing my org](https://www.chrisfarris.com/post/organization-cloudformation/). Caveat emptor.
### [Build event-driven applications with AWS CloudFormation StackSets event notifications in Amazon EventBridge](https://aws.amazon.com/about-aws/whats-new/2022/11/event-driven-applications-cloudformation-stacksets-event-notifications-eventbridge/)
Announced On: 2022-11-17
> Today, AWS CloudFormation StackSets launches event notifications via Amazon EventBridge. You can trigger event-driven actions after creating, updating, or deleting your CloudFormation stack sets. You can achieve this without developing or maintaining custom solutions that periodically poll for changes in your CloudFormation stack sets deployments via CloudFormation APIs. With this launch, you can build your event-driven applications across multiple AWS accounts, Organizational Units (OUs), and Regions with AWS CloudFormation StackSets and Amazon EventBridge.
Earlier this year, I spectacularly broke CloudFormation StackSets trying to deploy something across 200+ accounts and 17 regions. At the time, the best the service team could offer me around making their service self-managing was lambda to poll for stackset failures and then a very complex dance to either re-import broken stack instances or redeploy a single stack instance. Instead, I gave up and implemented a different solution. Having EventBridge support on stack instances is a big win for teams that use StackSets to push governance artifacts into all the accounts in their AWS Organization.
### [AWS Identity and Access Management now supports multiple multi-factor authentication (MFA) devices](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-identity-access-management-multi-factor-authentication-devices/)
Announced On: 2022-11-16
> AWS Identity and Access Management (IAM) now supports multiple multi-factor authentication (MFA) devices for root account users and IAM users in your AWS accounts. This provides additional flexibility and resiliency in your security strategy by enabling more than one authentication device per user. You can choose from one or more types of hardware and virtual devices supported by IAM.
This is an exciting one. The biggest issue with physical MFA tokens for root accounts is the fact that only _one person_ can have one. That was fine back in 2019 when we all worked in an office, but now everyone is remote, and that one token at that one engineer's house is a single point of failure.
### [AWS CloudTrail announces delegated administrator account support for AWS Organizations](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-cloudtrail-delegated-account-support-aws-organizations/)
Announced On: 2022-11-08
> Today, AWS CloudTrail announces support for a delegated administrator account, which provides customers with the ability to manage organization trails and CloudTrail Lake event data stores from an account other than the management account in AWS Organizations. Delegated administrator support enables flexibility for customers by allowing the management account to delegate CloudTrail administrative actions to an organization member account, such as their security and logging member account. With this feature, the management account of an organization remains the owner of all CloudTrail organization resources, even when those organization trails or CloudTrail Lake event data store resources are created and managed through the delegated administrator account. This helps customers with maintaining continuity of organization-wide CloudTrail audit logs, avoiding any disruption when changes are made to their organization in AWS Organizations.
I'm gonna be the contrarian here. You do not want to delegate the administration of CloudTrail. It's one of the few services that you should turn on (using [Organization Level CloudTrail](https://docs.aws.amazon.com/awscloudtrail/latest/userguide/creating-trail-organization.html)), and then _never_ touch again. New accounts will automatically be added to the CloudTrail, and closed accounts will be removed. The only use-case for this delegated admin is if you're using CloudTrail Lake, and want to run that outside of the payer (which you should do).
Here is the [AWS Blog post](https://aws.amazon.com/blogs/mt/enable-cross-account-queries-on-aws-cloudtrail-lake-using-delegated-administration-from-aws-organizations/?ck_subscriber_id=1874843840) on this release.
### [AWS Config now supports 14 new resource types](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-config-supports-14-resource-types/)
Announced On: 2022-11-09
> AWS Config now supports 14 more resource types for services including AWS IoT Events, AWS Cloud Map, Amazon EventBridge, EC2 Image Builder, AWS DataSync, AWS Glue, Amazon Route 53, and Amazon Elastic Container Registry.
I've [posted](https://www.chrisfarris.com/post/rethinking-config/) about AWS Config [a few times](https://www.chrisfarris.com/post/multi-account-config/), and I have to admit, one of my big complaints about the service - it only supports a handful of resource types - seems to have been somewhat resolved. The [complete list of services supported](https://docs.aws.amazon.com/config/latest/developerguide/resource-config-reference.html) is pretty comprehensive now. Unfortunately, it is still super hard to determine what it will cost to enable it.
## Anti-ransomware and disaster recovery announcements
### [Amazon Cognito now provides user pool deletion protection](https://aws.amazon.com/about-aws/whats-new/2022/10/amazon-cognito-console-user-pool-deletion-protection/)
Announced On: 2022-10-24
> You can now activate deletion protection for your Amazon Cognito user pools. Deletion protection prevents you from requesting the deletion of a user pool unless you first modify the pool and deactivate deletion protection.
Cognito has always been a scary service for storing customer account information. It's hard to back up, you can't port the data out, and the AWS customer doesn't manage even password resets. Adding a new API call to enable/disable deletion allows security administrators to apply a Service Control Policy to add a layer of protection around this critical resource.
### [AWS Backup now supports restore of VMware workloads to Amazon EC2](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-backup-restore-vmware-workloads-amazon-ec2/)
Announced On: 2022-11-11
> AWS Backup now supports restoring VMware backups to Amazon EC2. This allows you to restore your VMware backups directly in EC2, as EC2 native instances. AWS Backup can restore to on-premises VMware, VMware CloudTM on AWS Outposts, VMware Cloud on AWS, and Amazon Elastic Block Store (EBS). AWS Backup also supports restoring virtual machines (VMs) at the VM-level or disk-level.
This has some useful implications for site-wide Disaster Recovery. Did a hurricane just wipe out your data center? Now you can restore it all back in the cloud rather than leasing a new location and sourcing new servers.
## IAM
### [IAM Access Analyzer findings now support Amazon SNS topics and five other AWS resource types to help you identify public and cross-account access](https://aws.amazon.com/about-aws/whats-new/2022/10/iam-access-analyzer-findings-amazon-sns-topics-5-aws-resource-types-account-access/)
Announced On: 2022-10-26
> [AWS Identity and Access Management (IAM) Access Analyzer](https://docs.aws.amazon.com/IAM/latest/UserGuide/what-is-access-analyzer.html) now supports six additional resource types to help you identify public and cross-account access from outside your AWS account and organization. These six resource types include Amazon SNS topics, Amazon EBS volume snapshots, Amazon RDS DB snapshots, Amazon RDS DB cluster snapshots, Amazon ECR repositories, and Amazon EFS file systems. IAM Access Analyzer now analyzes resource policies, access control lists, and other access controls for these resources to make it easier for you to identify public, cross-account, and cross-organization access. These findings can help you adhere to the security best practice of least privilege and reduce unintended external access to your resources.
This is a pretty big improvement. Before this announcement, IAM Access Analyzer only looked resource policies. Now it's discovering publicly shared snapshots and resources that aren't made public via resource policies. IAM Access Analyzer is free. It works across organizations. It warns you about your bucket negligence award nominations. [Pickles](https://twitter.com/bjohnso5y/status/1576380924266442757) demands you start using it.
### [AWS IAM Identity Center now supports session management capabilities for AWS Command Line Interface (AWS CLI) and SDKs ](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-iam-identity-center-session-management-aws-cli-sdks/)
Announced On: 2022-11-21
> Starting today, AWS IAM Identity Center (successor to AWS Single Sign-On) customers can manage the session duration (between 15 mins and 7 days) for AWS Command Line Interface (AWS CLI) and SDKs sessions. With this release, when you set access portal session duration for your organization in IAM Identity Center, it also applies to AWS CLI and SDKs sessions in addition to application and console sessions.
I don't have strong opinions on the session duration here. Much will depend on how well your organization manages engineer's endpoints from an EDR/XDR perspective. The tokens an attacker needs to generate their own IAM credentials are still stored in `~/.aws/`, they're just not as obvious for a neophyte attacker.
## Networking & Compute
### [AWS Nitro System now supports previous generation of instances](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-nitro-system-supports-previous-generation-instances/)
Announced On: 2022-11-18
> Amazon Web Services announces AWS Nitro System support for EC2’s previous generation of instances to extend the length of service beyond the typical lifetime of the underlying hardware. The AWS Nitro System provides modern hardware and software components for EC2 instances, allowing customers to continue running their workloads and applications on the instance families they were built on without any service life concerns.
AWS is seamlessly transitioning older instance types to Nitro. This means that capabilities like VPC Traffic Mirroring, which were only available for some instance types when it launched, will eventually become supported. This is one worth watching.
### [Amazon EC2 enables easier patching of guest operating system and applications with Replace Root Volume](https://aws.amazon.com/about-aws/whats-new/2022/10/amazon-ec2-enables-patching-guest-operating-system-application-replace-root-volume/)
Announced On: 2022-10-27
> Starting today, Amazon EC2 supports the replacement of instance root volume using an updated AMI without requiring customers to stop their instance. This allows customers to easily update their applications and guest operating system, while retaining the instance store data, networking and IAM configuration.
This one is pretty cool. It's not precisely hot-swapping the root drive, as you _do_ need a reboot, but your VPC public IP address isn't lost, and if you're leveraging ephemeral volumes, you don't lose that data. Anything that makes it easier to patch your systems is a win.
### [Amazon EC2 enables you to opt out of directly shared Amazon Machine Images](https://aws.amazon.com/about-aws/whats-new/2022/11/amazon-ec2-opt-out-shared-amazon-machine-images/)
Announced On: 2022-11-04
> Starting today, you can remove your AWS account from launch permissions for an Amazon Machine Image (AMI) that was directly shared with your AWS account. You can leverage this capability, for example, to reduce the likelihood of launching an EC2 instance with an unused or deprecated AMI that was shared with you earlier.
"Oh, you signed up for a WordPress AMI which wasn't vetted by the vendor-risk team? Let's just un-share that with you while we check that for bitcoin mining malware." It would allow a central governance or security team to remove the ability for an ops team to leverage an AMI shared with them.
### [Amazon EC2 enables customer created tags to be included during image copy](https://aws.amazon.com/about-aws/whats-new/2022/11/amazon-ec2-enables-customer-created-tags-included-during-image-copy/)
Announced On: 2022-11-18
> Starting today, Amazon EC2 enables customer created tags to be included during Amazon Machine Image (AMI) CopyImage operations. This feature aims to reduce customer burden if you want to employ the same tags across all your copied AMIs. Previously, when you created a copy of an AMI, any tags you created for that AMI did not get copied over to the new AMI. You had to apply the tags to the new AMI manually after it was created if you wanted to replicate the same tags from the original AMI.
One of the issues I've got with the concept of ABAC is how sporadically the different AWS service support tag-on-create and tag-on-copy. More announcements like this, please.
### [AWS Firewall Manager can now import existing AWS Network Firewall resources](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-firewall-manager-import-existing-aws-network-firewall-resources/)
Announced On: 2022-11-08
> Starting today, AWS Firewall Manager supports Import Existing Network Firewall feature that enables customers to discover existing AWS Network Firewalls and bring them under the central management of AWS Firewall Manager. With this feature, you can see your security coverage provided by existing firewalls across AWS organizations and manage those firewalls without having to instantiate new ones.
### [Amazon NAT Gateway Now Allows You to Select Private IP Address for Network Address Translation](https://aws.amazon.com/about-aws/whats-new/2022/11/amazon-nat-gateway-allows-select-private-ip-address-network-address-translation/)
Announced On: 2022-11-17
> Starting today, you can choose the private IP address that your NAT Gateway uses for network address translation. Before this launch, your NAT Gateway would select a random private IP address from the subnet it is created in. As a result, customers who use NAT Gateway to access their partner networks were required to allowlist the entire subnet CIDR of the NAT Gateway.
### [Amazon Virtual Private Cloud (VPC) now supports the transfer of Elastic IP addresses between AWS accounts](https://aws.amazon.com/about-aws/whats-new/2022/10/amazon-virtual-private-cloud-vpc-transfer-elastic-ip-addresses-between-aws-accounts/)
Announced On: 2022-10-31
> Today, we are announcing Elastic IP transfer, a new Amazon VPC feature that allows you to transfer your Elastic IP addresses from one AWS Account to another, making it easier to move Elastic IP addresses during AWS Account restructuring.
Too many companies live in a single AWS account because decomposing your enterprise into multiple accounts is bloody hard. Moving EIPs would help this migration of resources from the multi-tenant swamp into cleaner team or application-centric accounts. However, moving EIPs also introduces the idea of moving EIPs into accounts that don't belong to you.
My challenge to AWS on this is: Now do S3 Buckets.
## Encryption
### [AWS Certificate Manager now supports Elliptic Curve Digital Signature Algorithm TLS certificates](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-certificate-manager-elliptic-curve-digital-signature-algorithm-tls-certificates/)
Announced On: 2022-11-08
> You can now use AWS Certificate Manager (ACM) to request and use Elliptic Curve Digital Signature Algorithm (ECDSA) P-256 and P-384 Transport Layer Security (TLS) certificates to secure your network traffic. TLS certificates are used to secure network communications and to establish the identity of websites over the internet as well as resources on private networks. ACM lets you easily provision, manage, and deploy public and private TLS certificates. You can learn more about ECDSA security, performance and compatibility in this AWS Security blog post.
Math is hard, but I'm told elliptic curves are easier than prime numbers. At the scale AWS operates, this could have a non-trivial impact of CO2 output.
### [AWS CloudTrail Lake now supports encryption using Customer Managed KMS Keys (CMK)](https://aws.amazon.com/about-aws/whats-new/2022/11/cloudtrail-lake-supports-encryption-customer-managed-kms-keys-cmk/)
Announced On: 2022-11-11
> AWS CloudTrail announces the ability to use your own Customer Managed KMS Keys (CMK) to encrypt the activity logs stored in CloudTrail Lake. CloudTrail has always provided encryption by default using AWS owned KMS keys for all data stored in CloudTrail Lake. This feature provides you the option of adding a self-managed security layer to your activity logs to help you meet the compliance and regulatory requirements of your organization.
I once made the mistake of writing "... must be encrypted with a Customer Managed Keys (CMK)" in an AWS Baseline. If someone in your organization once made that same mistake, this service is now open for you to use.
## Compliance
### [AWS Audit Manager now provides search-based filtering and grouping to help with noncompliance root-cause analysis](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-audit-manager-search-based-filtering-grouping-root-cause-analysis/)
Announced On: 2022-11-18
> AWS Audit Manager automatically collects evidence data, via snapshots of user activity or resource configurations, against controls that customers want to evaluate. Now, Audit Manager more easily allows you to sift through thousands of pieces of this collected evidence from multiple disparate sources, using search filters and groupings to identify trends and cross-reference issues. This will help you deep dive into issues identified via flagged compliance checks in the service, either in assessments - an automated data collection process against a specific set of controls - or on the Audit Manager dashboard. With this feature, you can filter and group evidence data using parameters like controls, resource types or resource IDs, service, event names, account IDs, etc. to understand the drivers of the issue. These results can then be exported as audit-ready PDF reports.
If this announcement materially impacted my day-to-day job, I'd probably leave IT and take up alpaca farming. However, if you need to collect this level of compliance information, you've got something to help.
## Storage & Serverless
### [Amazon S3 Storage Lens increases organization-wide visibility with 34 new metrics ](https://aws.amazon.com/about-aws/whats-new/2022/11/amazon-s3-storage-lens-organization-wide-visibility-34-metrics/)
Announced On: 2022-11-17
> Amazon S3 Storage Lens is a cloud storage analytics feature that delivers organization-wide visibility into object storage usage and activity. Today, 34 additional metrics have been added to uncover deeper cost optimization opportunities, identify data protection best practices, and improve the performance of application workflows.
One of the more interesting metrics introduced is 403 authorization failures. This allows you to measure and alert on who is trying to access data in your bucket that lacks the authorization to do so. Unfortunately, that's an advanced metric that's [priced at](https://aws.amazon.com/s3/pricing/#aws-element-1b262844-037a-45d9-baf7-024401891ece) $0.20 per million objects monitored per month.
### [AWS Secrets Manager increases the API Requests per Second limits](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-secrets-manager-increases-api-requests-per-second-limits/)
Announced On: 2022-11-11
> AWS Secrets Manager now supports higher request rates for the core set of API operations - GetSecretValue, DescribeSecret and ListSecrets. The request rate limits for GetSecretValue and DescribeSecret have been increased to 10,000 requests per second. The request rate of ListSecrets API operation has been increased to 100 requests per second. No action is required on your part, these increased API limits are available at no additional cost and will automatically be applied to your AWS accounts. These limit increases makes it easier for you to scale your Secrets Manager operations.
I'm reminded of [Corey's](https://www.lastweekinaws.com/blog/aws-re-invent-what-you-actually-need-to-know-before-you-go/) "All releases are for someone, no release is for everyone" adage, and I'm curious about the use case for requesting a secret 10k times per second. If this feature applies to you, I'll buy you a beer in Vegas and let you unload on your unfortunate situation.
### [AWS Chatbot now supports command aliases to shorten frequently used AWS CLI commands in Slack](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-chatbot-command-aliases-shorten-cli-commands-slack/)
Announced On: 2022-11-18
> Today, AWS announces the general availability of the command aliases feature in AWS Chatbot, which allows you to use shortcuts to reference AWS Command Line Interface (CLI) commands in Slack. Command aliases allows you run frequently used commands quickly and reduces typing errors. With this feature you can now create aliases for your routine AWS CLI commands and run these alias commands directly from your Slack channels. The aliases can be configured to include one or more custom parameters. To use a command alias, you just type “@aws run <alias\_name>” in the chat channel. Command aliases run under the configured channel permissions and no additional permissions management is required.
This is an interesting iterative feature on top of the existing Chatbot service. However, it's worth highlighting again that Chatbot takes AWS control-plane authentication and authorization outside the scope of IAM and into an entirely new cloud service. Are you managing the access and controls of your slack environment with the same rigor you manage access to AWS IAM?
### [Simplify cross-account access for your AWS services with AWS Step Functions](https://aws.amazon.com/about-aws/whats-new/2022/11/simplify-cross-account-access-aws-services-step-functions/)
Announced On: 2022-11-18
> AWS Step Functions now supports cross-account access for more than 220 AWS services so it’s easier to process data, automate IT and business processes, and build applications across accounts.
State machine definitions can now specify a cross-account role arn to invoke a task in another AWS account.
## AWS WAF & CloudFront
I don't have much to say about AWS WAF. It's better than nothing, but strong security teams are using technologies that are better.
* [AWS WAF launches Challenge rule action and Bot Control for Targeted Bots](https://aws.amazon.com/about-aws/whats-new/2022/10/aws-waf-challenge-rule-action-bot-control-targeted-bots/)
* [AWS WAF Now Supports Granular Geographic Match](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-waf-supports-granular-geographic-match/)
* [Amazon CloudFront now supports JA3 fingerprint headers](https://aws.amazon.com/about-aws/whats-new/2022/11/amazon-cloudfront-supports-ja3-fingerprint-headers/)
## AWS Security Hub
I'm not a big proponent of Security Hub. It's an AWS-centric solution that requires AWS Config Service (see comment about estimating the costs of Config).
* [AWS Security Hub now supports bidirectional integration via AWS Service Management Connector for Atlassian’s Jira Service Management Cloud](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-security-hub-bidirectional-integration-connector-atlassians-jira-management-cloud/)
* [Monitor your IoT application’s security posture in AWS Security Hub, now integrated with AWS IoT Device Defender](https://aws.amazon.com/about-aws/whats-new/2022/11/aws-security-hub-iot-device-defender-application-security-posture/)
* [AWS Security Hub launches support for the Center for Internet Security’s (CIS) AWS Foundations Benchmark version 1.4.0](https://aws.amazon.com/about-aws/whats-new/2022/11/security-hub-center-internet-securitys-cis-foundations-benchmark-version-1-4-0/)
The CIS Benchmark for [AWS v1.5.0 came out over the summer](https://steampipe.io/blog/cis-v15-aws-benchmark). I will say that if you're looking for an off-the-shelf baseline to use for your Cloud Security efforts in AWS, I would recommend the [AWS Foundational Security Best Practices standard](https://docs.aws.amazon.com/securityhub/latest/userguide/securityhub-standards-fsbp.html).
## Closing
That's it. No big security tools or features announced. Maybe they'll drop tonight and I'll update this post, or maybe they're being held in reserve for re:Invent proper. Either way, I'll be back the week after re:Invent to cover any interesting announcements that might have been missed in the excitement of re:Invent.