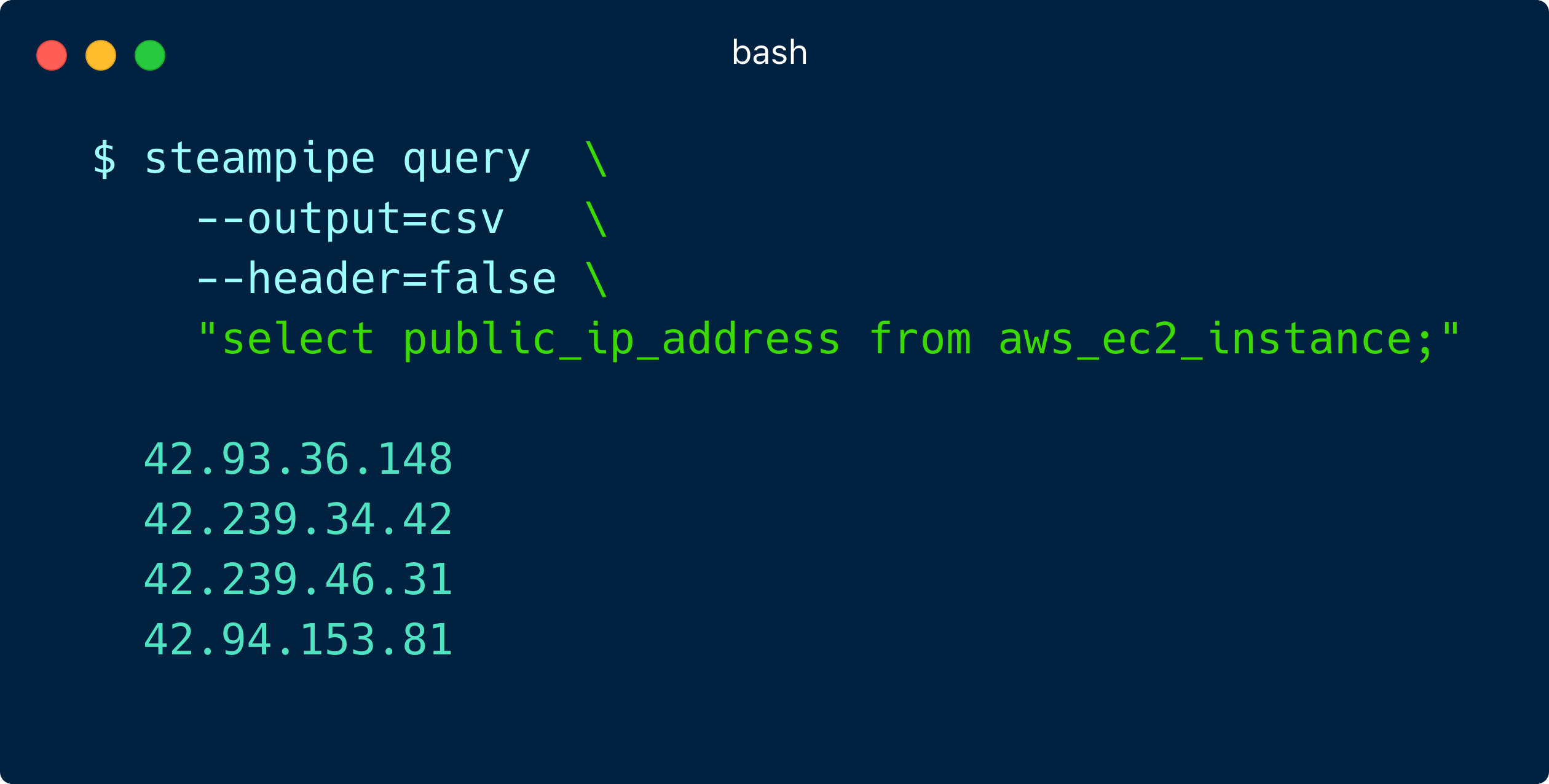
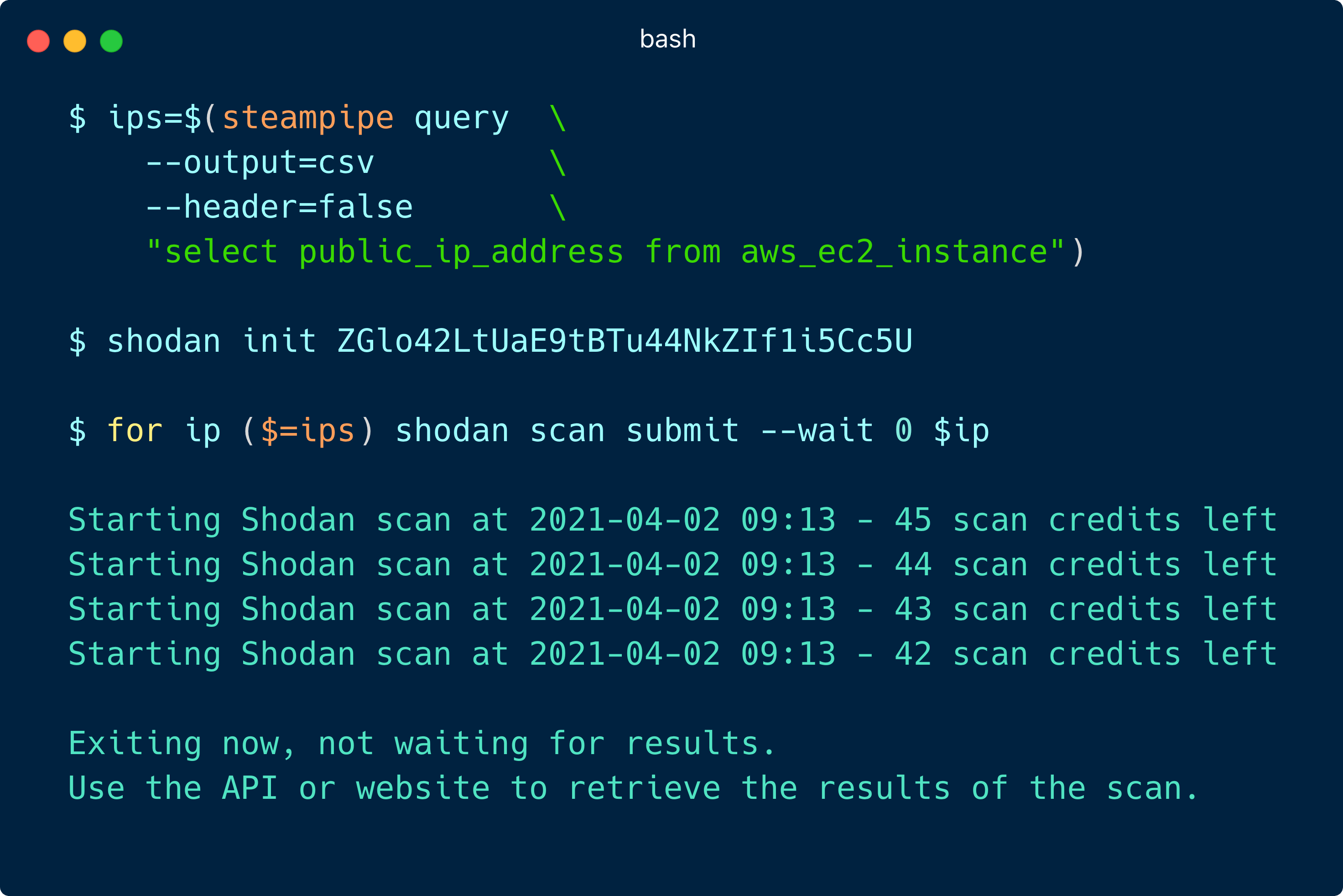
## Other [#shiftleftjoin](https://twitter.com/search?q=%23shiftleftjoin) opportunities with Shodan: #### What TLS ciphers are enabled on my load balancers?
## Thank you Shodan Team! We think it is incredible to have such a useful service to integrate with for security testing against dynamic cloud environments. A huge shout out to the entire [Shodan team](https://twitter.com/shodanhq) for making it accessible via their API.